Check Point Software SWOT Analysis
Fully Editable
Tailor To Your Needs In Excel Or Sheets
Professional Design
Trusted, Industry-Standard Templates
Pre-Built
For Quick And Efficient Use
No Expertise Is Needed
Easy To Follow
Check Point Software Bundle
Check Point Software boasts strong brand recognition and a comprehensive security portfolio, but faces intense competition and evolving threat landscapes. Our full SWOT analysis delves into these critical factors, providing you with a deeper understanding of their market position and future trajectory.
Want the full story behind Check Point's competitive advantages, potential vulnerabilities, and growth opportunities? Purchase the complete SWOT analysis to gain access to a professionally written, fully editable report designed to support your strategic planning and investment decisions.
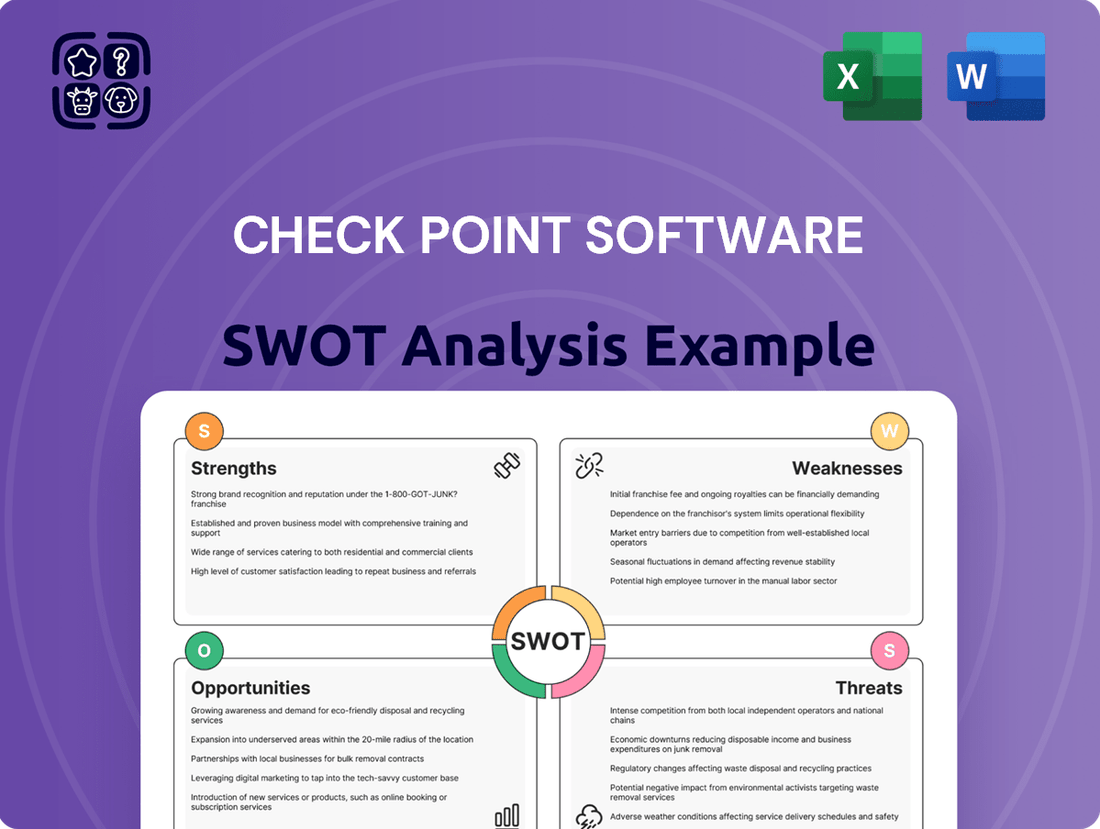
Strengths
Check Point Software boasts a remarkably comprehensive security portfolio, addressing network, endpoint, cloud, mobile, and data security needs, along with robust security management capabilities. This breadth allows them to serve a wide array of clients, from large corporations to smaller businesses, offering a unified security posture through their Infinity Platform.
Check Point's core strength lies in its advanced AI capabilities, driving a prevention-first cybersecurity strategy. This approach aims to identify and neutralize threats before they can impact systems, a crucial advantage in today's rapidly evolving threat landscape.
The company's AI-powered solutions, including Infinity AI Copilot and ThreatCloud AI, are engineered for superior threat detection and rapid response. These technologies are designed to achieve industry-leading catch rates, ensuring a robust defense against sophisticated cyberattacks.
Check Point Software has consistently shown robust financial performance, marked by steady revenue increases and healthy profit margins. This financial strength is a significant advantage.
For example, in the second quarter of 2025, the company reported a 6% rise in total revenues compared to the same period in the previous year. More impressively, revenues from products and licenses grew by 12%, highlighting strong customer adoption and demand for their advanced security solutions.
Recognized Industry Leader
Check Point Software is widely acknowledged as a frontrunner in the cybersecurity sector, a status reinforced by numerous industry accolades. This consistent recognition from respected entities underscores their commitment to innovation and market leadership.
Their leadership has been particularly noted in key areas:
- Forrester Wave: Zero Trust Platforms Check Point has been named a leader, highlighting their comprehensive approach to securing modern networks and data.
- GigaOm Radar for Anti-Phishing Solutions The company's effectiveness in combating phishing attacks has earned them a prominent position in this evaluation.
- Newsweek's America's Best Cybersecurity Companies Inclusion on this list further solidifies their reputation as a trusted provider of advanced security solutions within the US market.
Focus on Innovation and Strategic Acquisitions
Check Point Software Technologies consistently demonstrates a strong commitment to innovation, a key strength that allows them to stay ahead in the cybersecurity sector. This focus is evident in their ongoing development of advanced security engines and their proactive approach to strategic acquisitions. For instance, in 2024, Check Point continued to bolster its offerings through targeted acquisitions, enhancing its comprehensive Infinity architecture.
These strategic moves are crucial for maintaining a competitive edge. By integrating new technologies and expertise, Check Point expands its platform's capabilities. Acquisitions like Veriti and Cyberint, which were integrated into their operations, significantly strengthened their threat exposure management and enterprise risk management solutions. This proactive integration ensures their platform remains robust against the ever-changing and sophisticated threat landscape.
The company's investment in research and development is substantial, fueling the creation of cutting-edge security solutions. This dedication to innovation is not just about product development; it's about anticipating future threats and building defenses accordingly. For example, their ongoing advancements in areas like cloud security and AI-driven threat detection underscore this commitment.
- Continuous R&D Investment: Check Point consistently allocates significant resources to research and development, fostering the creation of novel security technologies.
- Strategic Acquisition Approach: The company actively pursues acquisitions to integrate complementary technologies and expertise, thereby enhancing its core Infinity platform.
- Expansion of Capabilities: Recent acquisitions have broadened Check Point's offerings in critical areas such as threat exposure management and enterprise risk management.
- Adaptability to Threat Landscape: This focus on innovation and acquisition allows Check Point to effectively adapt to and counter the evolving nature of cyber threats.
Check Point's comprehensive security portfolio, spanning network, endpoint, cloud, and mobile security, is a significant strength, enabling them to offer a unified defense through their Infinity Platform. Their leading position in cybersecurity is further solidified by consistent industry recognition, including being named a leader in Forrester Wave for Zero Trust Platforms and appearing on Newsweek's America's Best Cybersecurity Companies list.
The company's financial health is robust, with consistent revenue growth. For instance, Q2 2025 saw a 6% increase in total revenues year-over-year, with products and licenses revenue jumping an impressive 12%, indicating strong market demand for their advanced solutions.
Check Point's commitment to innovation, demonstrated through substantial R&D investment and strategic acquisitions like Veriti and Cyberint, allows them to continuously enhance their platform and adapt to the evolving threat landscape, particularly in areas like AI-driven threat detection.
Their prevention-first cybersecurity strategy, powered by advanced AI and solutions like Infinity AI Copilot and ThreatCloud AI, is a key differentiator, aiming for industry-leading threat catch rates and rapid response capabilities.
What is included in the product
Analyzes Check Point Software’s competitive position through key internal and external factors, highlighting its strengths in advanced threat prevention and opportunities in cloud security, while acknowledging weaknesses in market share and threats from evolving cyberattack landscapes.
Offers a clear, actionable SWOT analysis to pinpoint and address Check Point's strategic challenges.
Weaknesses
While Check Point Software is a major force in cybersecurity, its market share, though substantial, is notably smaller than giants like Broadcom (which acquired Symantec's enterprise business) and Trellix (formed from McAfee Enterprise and FireEye). This disparity highlights the ongoing challenge of capturing a larger slice of the vast cybersecurity market, especially in areas where these larger competitors have established deep roots and extensive product portfolios.
Despite Check Point's focus on prevention, the escalating global cyber-attack landscape, marked by a 44% year-over-year increase in incidents as highlighted in their 2025 Security Report, might lead some clients to question the ultimate efficacy of even advanced cybersecurity measures. This surge in sophisticated threats, often bypassing traditional defenses, could create customer confidence concerns regarding the ability of any single solution to provide complete protection.
The cybersecurity landscape is rapidly evolving with AI-powered threats. We're seeing more sophisticated phishing attacks, malware that adapts in real-time, and even deepfake impersonations designed to trick users. This presents a significant challenge for any security provider.
While Check Point leverages AI in its own defenses, the sheer pace and increasing complexity of adversarial AI could put a strain on their ability to consistently maintain a leading edge. Staying ahead of these constantly evolving, AI-driven attacks requires continuous innovation and significant investment.
Impact of Acquisition-Related Costs on Cash Flow
Check Point's growth strategy through acquisitions, while aiming to expand its capabilities, presents a significant drain on its cash flow. These strategic moves, such as the acquisitions of Cyberint and Veriti during 2024 and 2025, require substantial upfront cash investments. This outflow can temporarily reduce the company's available cash reserves, potentially affecting its short-term liquidity or its capacity to fund other growth initiatives or operational needs.
The financial impact of these acquisition-related costs needs careful management. For instance, while specific figures for the full cash impact of the Cyberint and Veriti deals are still emerging in the 2024-2025 period, similar past transactions indicate that such integrations can lead to notable decreases in cash balances. This necessitates robust financial planning to ensure that these strategic investments do not compromise the company's overall financial health or its ability to invest in organic growth and innovation.
- Significant Cash Outlays: Acquisitions like Cyberint and Veriti in 2024-2025 represent substantial cash expenditures.
- Impact on Liquidity: These cash outflows can temporarily reduce available cash balances, potentially impacting short-term liquidity.
- Future Investment Capacity: A decrease in cash reserves might limit future investment opportunities or the company's financial flexibility.
- Need for Financial Management: Effective management of acquisition costs is crucial to maintain financial stability and support ongoing operations.
Dependence on Channel Partners for SMB Market
Check Point's penetration into the Small and Medium-sized Business (SMB) market is significantly influenced by its network of channel partners and Managed Service Providers (MSPs). This reliance, while a standard practice in the industry, creates a vulnerability. The company's success in reaching and serving SMBs is directly tied to the performance, dedication, and technical proficiency of these external partners.
This dependence means that any limitations or shifts in partner strategy can directly impact Check Point's market share and customer satisfaction within the SMB segment. For instance, if a key partner decides to prioritize other vendors or experiences operational challenges, Check Point's SMB outreach can be significantly hampered. This highlights a critical weakness in their go-to-market strategy for this vital customer base.
The effectiveness of Check Point's SMB strategy is therefore contingent upon:
- Partner Enablement: Ensuring partners are adequately trained and equipped to sell and support Check Point solutions.
- Partner Alignment: Maintaining strong relationships and shared strategic goals with channel partners.
- Partner Performance: Monitoring and addressing any underperformance among key partners.
Check Point's market share, while significant, trails behind major competitors like Broadcom and Trellix, indicating a persistent challenge in capturing a larger portion of the expansive cybersecurity market. This competitive pressure is particularly acute in areas where larger players have deeply entrenched product offerings and established client relationships.
The company's reliance on channel partners for SMB market penetration presents a vulnerability. The success of this strategy is directly tied to partner performance, dedication, and technical capabilities, meaning any shortcomings or strategic shifts by these partners can directly impede Check Point's reach and customer satisfaction in this crucial segment.
Preview the Actual Deliverable
Check Point Software SWOT Analysis
This preview reflects the real document you'll receive—professional, structured, and ready to use. You're seeing the actual Check Point Software SWOT analysis, providing a clear understanding of their strategic position. Upon purchase, you'll gain access to the complete, detailed report.
Opportunities
The massive shift of businesses to cloud platforms, alongside increasing cloud security risks, creates a prime opportunity for Check Point. As more data and operations move online, the need for robust protection intensifies.
This trend is directly fueling the demand for cloud security solutions. Analysts project cloud security spending to climb significantly in 2024 and 2025, a market where Check Point's CloudGuard is well-positioned to thrive, catering to complex hybrid, multi-cloud, and SaaS setups.
The escalating complexity of cyber threats, increasingly powered by artificial intelligence, creates a significant demand for sophisticated AI-driven cybersecurity solutions. This trend directly fuels the market opportunity for companies like Check Point.
Check Point is well-positioned to leverage its established AI expertise, particularly with offerings like Infinity AI Copilot. This allows them to develop and enhance AI-first detection and enforcement tools, directly addressing the evolving threat landscape and providing advanced protection for organizations.
The global shift towards Zero Trust security frameworks is a major tailwind for Check Point. As organizations increasingly prioritize robust data protection and regulatory adherence, the demand for comprehensive Zero Trust solutions is soaring. Gartner predicts the Zero Trust security market to reach $49.5 billion by 2027, a substantial increase from previous years.
Check Point's established leadership in this space, particularly its unified and prevention-first strategy, directly addresses this burgeoning market. Their integrated platform, offering advanced threat prevention and granular access control, is perfectly aligned with the evolving security needs of enterprises worldwide, making it a key growth driver.
Addressing Cybersecurity Skills Shortage
The persistent global cybersecurity skills shortage presents a significant opportunity for Check Point. Many organizations struggle to find and retain qualified cybersecurity professionals, leading to increased vulnerability. For instance, (ISC)² reported in 2023 that the cybersecurity workforce needed to grow by 70% to effectively defend organizations.
Check Point can capitalize on this by expanding its managed security services, offering clients a way to outsource their security operations and gain access to expert talent. This allows companies to bolster their defenses without the internal hiring challenges. Furthermore, simplifying its platform and integrating advanced automation can further alleviate the burden on understaffed IT departments.
By providing these solutions, Check Point can not only address a critical market need but also expand its service offerings and capture a larger share of the managed security services market, which is projected to reach $60.1 billion by 2027, according to MarketsandMarkets.
- Address the critical cybersecurity talent gap.
- Expand managed security services to fill client needs.
- Leverage simplified platforms and automation to ease client burden.
- Capitalize on the growing managed security services market.
Targeting Emerging Threat Vectors like IoT and Supply Chain
The proliferation of Internet of Things (IoT) devices and the intricate nature of modern supply chains present a fertile ground for cyber threats. This evolving landscape creates a significant opportunity for Check Point to expand its security offerings, focusing on these increasingly targeted areas.
Check Point can capitalize on the growing demand for robust IoT security solutions. As more devices connect, the attack surface expands, making specialized protection crucial. Similarly, safeguarding complex supply chains against disruption and data breaches is paramount for businesses worldwide.
- IoT Security Growth: The global IoT security market is projected to reach $22.4 billion by 2026, indicating substantial growth potential.
- Supply Chain Vulnerabilities: A 2023 report highlighted that 77% of organizations experienced a supply chain attack, underscoring the critical need for enhanced protection.
- Targeted Solutions: Developing advanced threat intelligence and tailored security platforms for IoT ecosystems and supply chain logistics can address these emerging risks.
The continuing digital transformation, especially the move to cloud environments, significantly boosts the need for advanced cybersecurity. Check Point's cloud security solutions, like CloudGuard, are well-positioned to meet this growing demand as businesses increasingly rely on hybrid and multi-cloud infrastructures.
The rising sophistication of cyberattacks, often leveraging AI, creates a substantial market for AI-powered security. Check Point's Infinity AI Copilot directly addresses this by offering advanced threat detection and prevention, aligning with the market's need for intelligent security.
The widespread adoption of Zero Trust security frameworks presents a key opportunity for Check Point. Their integrated platform, emphasizing prevention and granular control, perfectly aligns with organizational goals for enhanced data protection and compliance, a market expected to grow substantially.
Check Point can capitalize on the global cybersecurity skills shortage by expanding its managed security services. This addresses the critical need for expert security personnel, allowing organizations to outsource their security operations and benefit from Check Point's expertise, tapping into the expanding managed services market.
Threats
The cybersecurity battleground is constantly evolving, with cyber attackers becoming incredibly sophisticated. We're seeing more AI-powered phishing attempts, malware that adapts in real-time, and advanced ransomware that can lock down entire systems. This means companies like Check Point have to innovate at a breakneck pace just to keep up.
This escalating threat environment puts significant pressure on Check Point's research and development efforts. They need to constantly push the boundaries of their technology to counter new attack vectors. For instance, in 2023, the average cost of a data breach reached an all-time high of $4.45 million globally, underscoring the critical need for robust defenses.
Check Point Software operates in a fiercely competitive cybersecurity landscape, facing off against both long-standing giants and nimble startups. This intense rivalry means constant pressure to innovate and maintain market relevance.
Established competitors such as Palo Alto Networks, Microsoft, and Fortinet are actively pursuing growth through acquisitions and significant investments in AI-powered threat detection. For instance, Palo Alto Networks' acquisition of CloudGenix in 2021 for $420 million bolstered its SASE capabilities, a key area of competition.
These aggressive strategies by rivals could potentially erode Check Point's market share and limit its pricing flexibility. The cybersecurity market is dynamic, with companies like CrowdStrike also making substantial gains, reporting a 32% year-over-year revenue increase in Q1 2024, highlighting the rapid pace of change and competitive pressures.
The increasing complexity and interconnectedness of global supply chains present a significant challenge for cybersecurity firms like Check Point. This intricate web of suppliers and partners, while often necessary for efficiency, creates a less transparent and more unpredictable environment for managing security risks. A breach at any point in this chain can have cascading effects.
Check Point, like its peers, is susceptible to its own supply chain being compromised. This could involve malicious code being inserted into software components or hardware manufactured by third parties. Such an event could directly impact the security of Check Point's products and, by extension, the security of its customers' networks and data.
Furthermore, vulnerabilities within third-party vendors that Check Point relies upon for services or components pose a direct threat. If a partner experiences a security incident, it could inadvertently expose Check Point's intellectual property or customer data, or even create a backdoor into Check Point's own systems, ultimately undermining the trust placed in their security solutions.
Regulatory Compliance Burden and Evolving Privacy Laws
The increasing number of global regulations, especially around data privacy like the GDPR and CCPA, creates a substantial compliance challenge for businesses. This regulatory landscape directly impacts cybersecurity providers like Check Point, as they must ensure their solutions meet these evolving standards.
While these regulations can boost demand for advanced security, Check Point faces the ongoing cost and complexity of adapting its product portfolio to maintain compliance. For instance, the global cybersecurity market, driven partly by regulatory pressures, was projected to reach over $300 billion in 2024, highlighting the scale of this opportunity and the associated compliance demands.
- Increased Compliance Costs: Adapting security solutions to meet diverse and changing global data privacy laws requires significant investment in research, development, and legal expertise.
- Product Development Complexity: Ensuring that new and existing security features align with regulations such as GDPR, which carries fines up to 4% of global annual revenue, adds layers of complexity to product roadmaps.
- Market Access Challenges: Failure to comply with specific regional privacy laws can restrict market access and lead to substantial penalties, impacting revenue streams.
Potential for Data Breaches and Security Incidents Affecting Trust
Even cybersecurity leaders like Check Point face the persistent threat of data breaches. A reported hacking attempt in early 2025, though contained, underscores the inherent risks in the digital landscape. Such incidents, regardless of their scale, can significantly erode customer confidence, a critical asset for any security firm.
The potential fallout from a security incident for Check Point includes:
- Reputational Damage: A breach could lead to a perception that Check Point's own defenses are fallible, impacting its credibility.
- Loss of Customer Trust: Clients entrust Check Point with their sensitive data, making security incidents a direct threat to that relationship.
- Increased Scrutiny: Regulators and customers alike may impose stricter compliance demands following a security event.
The cybersecurity landscape is a constant arms race, with sophisticated threats like AI-driven phishing and advanced ransomware demanding rapid innovation. This dynamic environment, coupled with intense competition from giants like Palo Alto Networks and agile players like CrowdStrike, puts pressure on Check Point's market share and pricing power. Furthermore, the interconnectedness of global supply chains introduces vulnerabilities, as a compromise within a vendor could impact Check Point's own products and customer trust. The increasing complexity of global data privacy regulations, such as GDPR, also necessitates significant investment in compliance and product adaptation, posing a constant challenge to market access and revenue streams.
SWOT Analysis Data Sources
This analysis is built upon a foundation of credible data, including Check Point's official financial reports, comprehensive market research, and insights from industry experts and reputable technology publications.