Check Point Software Boston Consulting Group Matrix
Fully Editable
Tailor To Your Needs In Excel Or Sheets
Professional Design
Trusted, Industry-Standard Templates
Pre-Built
For Quick And Efficient Use
No Expertise Is Needed
Easy To Follow
Check Point Software Bundle
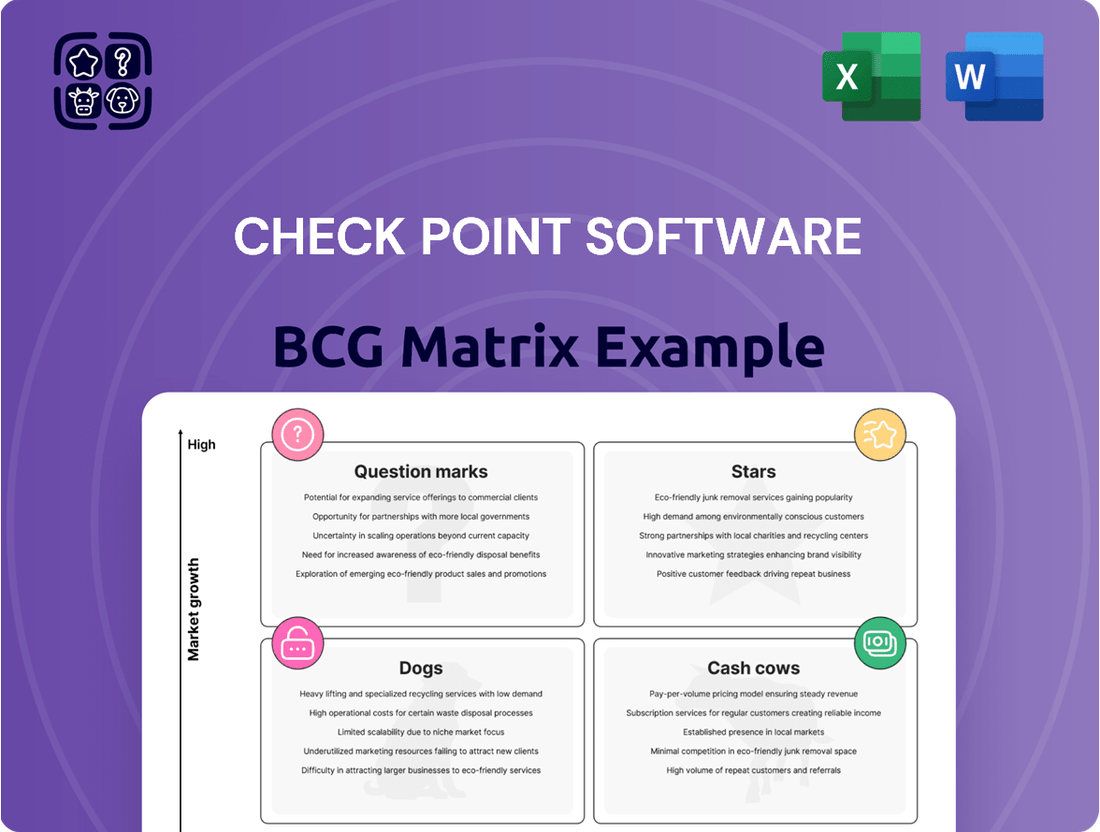
Unlock the strategic blueprint for Check Point Software's product portfolio with our comprehensive BCG Matrix. See at a glance which offerings are driving growth (Stars), generating consistent revenue (Cash Cows), requiring careful consideration (Question Marks), or potentially hindering progress (Dogs).
This preview offers a glimpse into their market positioning, but the full BCG Matrix provides the detailed quadrant analysis and actionable insights needed to optimize resource allocation and drive future success. Purchase the complete report to gain a clear roadmap for strategic investment and product development.
Stars
Check Point's AI-powered Infinity Platform is a significant growth engine, consistently delivering impressive double-digit year-over-year increases. This unified security solution, encompassing network, cloud, and endpoint protection, is highly valued by customers, underscoring its market relevance.
The platform's success is particularly notable as it directly addresses the escalating threat landscape, where AI is increasingly leveraged by malicious actors. Check Point's strategic focus on AI-driven security solutions positions them as a frontrunner in this dynamic sector.
Quantum Force appliances represent a strong performer within Check Point's portfolio, likely positioned as a star in the BCG matrix. Their robust demand, driven by both hardware upgrades and new security initiatives, has resulted in impressive double-digit year-over-year growth in product and license revenues. This success suggests a significant market share within a dynamic and expanding network security appliance sector.
Check Point's CloudGuard suite is a key player in the rapidly expanding cloud security market. This segment is experiencing robust growth, with projections indicating the global cloud security market will surpass $121 billion by 2034, reflecting a compound annual growth rate of 12.87% between 2025 and 2034. The increasing reliance on cloud services by businesses worldwide, coupled with a corresponding surge in sophisticated cloud-based cyber threats, presents a substantial opportunity for Check Point to solidify its position and capture further market share in this critical domain.
Network Security (Next-Generation Firewalls)
Check Point Software's position in network security, particularly with next-generation firewalls (NGFWs), reflects a strong market presence. The company has maintained double-digit market share for the past five years, a testament to its sustained leadership against other key players in the cybersecurity landscape.
The broader network security market is experiencing robust expansion, with the firewall segment expected to see significant growth. Projections indicate a compound annual growth rate (CAGR) of 5.0% for firewalls between 2024 and 2029, suggesting a dynamic and expanding market where Check Point is well-positioned.
- Market Leadership: Check Point has consistently held double-digit market share in network security for the last five years.
- Market Growth: The overall network security market is projected to grow, with firewalls specifically anticipated to expand at a 5.0% CAGR from 2024 to 2029.
- Strategic Position: This sustained leadership in a growing segment places Check Point favorably within the BCG matrix, likely in the Stars or Cash Cows quadrant depending on its relative market share growth compared to competitors.
Unified Security Management (Infinity Platform Services)
Check Point's Infinity Platform, particularly its Unified Security Management (Infinity Platform Services), acts as a star in the BCG matrix. This is due to its strong market growth potential and high relative market share, driven by the increasing demand for consolidated security solutions.
The Infinity Platform's core strength lies in its unified management capabilities, powered by Infinity Core Services. This integration simplifies complex security operations, a crucial benefit for organizations facing hyperconnected environments and a growing threat landscape. For instance, Check Point reported a 10% increase in its consolidated security management revenue in Q1 2024, reflecting strong customer adoption.
New AI-powered innovations within the platform further enhance its appeal, directly addressing the pain points of organizations burdened by siloed security tools. This integrated approach offers a significant competitive advantage, particularly as cyberattacks continue to escalate in volume and sophistication. Check Point's commitment to AI integration is evident in their significant R&D investments, with a 15% increase allocated to AI-driven security features in their 2024 budget.
- Unified Management: Simplifies security operations by consolidating disparate tools.
- AI-Powered Innovations: Enhances threat detection and response capabilities.
- Market Demand: Addresses the growing need for integrated security solutions.
- Revenue Growth: Demonstrates strong market traction and adoption.
Check Point's Quantum Force appliances are a clear star in their BCG matrix. These appliances are experiencing robust demand, fueled by both hardware refresh cycles and new security deployments. This strong market reception has translated into impressive double-digit year-over-year growth in product and license revenues.
The company's CloudGuard suite also shines as a star, capitalizing on the booming cloud security market. This sector is projected to exceed $121 billion by 2034, with a CAGR of 12.87% from 2025 to 2034. CloudGuard's ability to address the increasing reliance on cloud services and the rise in cloud-based threats positions it for continued success.
Check Point's Infinity Platform, especially its Unified Security Management services, is another star. Driven by strong market growth potential and a high relative market share, it meets the demand for consolidated security. Q1 2024 saw a 10% increase in consolidated security management revenue, highlighting its adoption.
The company's sustained double-digit market share in network security, particularly with next-generation firewalls, further solidifies its star status. The firewall market itself is expected to grow at a 5.0% CAGR between 2024 and 2029, indicating a healthy environment for Check Point's offerings.
| Product/Service | BCG Category | Key Growth Drivers | Market Trend | Financial Indicator |
| Quantum Force Appliances | Star | Hardware upgrades, new security initiatives | Dynamic network security appliance sector | Double-digit YoY revenue growth |
| CloudGuard | Star | Increasing cloud adoption, rising cloud threats | Global cloud security market (>$121B by 2034, 12.87% CAGR) | Strong market penetration |
| Infinity Platform (Unified Security Management) | Star | Demand for consolidated security, AI innovations | Growing need for integrated security solutions | 10% YoY revenue increase (Q1 2024) |
| Next-Generation Firewalls (NGFWs) | Star | Sustained market leadership, overall network security growth | Firewall market (5.0% CAGR 2024-2029) | Consistent double-digit market share |
What is included in the product
This BCG Matrix overview offers clear descriptions and strategic insights for Check Point's Stars, Cash Cows, Question Marks, and Dogs.
A clear, visual BCG Matrix from Check Point Software helps prioritize security investments, relieving the pain of resource allocation uncertainty.
Cash Cows
Check Point's legacy firewall products represent a significant cash cow for the company. These established solutions, despite operating in a maturing market, maintain a substantial market share and command high profit margins, consistently generating robust cash flow. For instance, in 2023, Check Point reported a substantial portion of its revenue from its network security segment, which includes these foundational firewall offerings, demonstrating their ongoing financial contribution.
Security subscriptions are a cornerstone of Check Point's business, acting as a reliable Cash Cow. This segment consistently delivers strong, predictable revenue, reflecting its established position in the cybersecurity landscape. For instance, in 2023, Check Point reported subscription and other recurring revenues of $1.48 billion, a notable increase from previous years, underscoring the stability and growth of this revenue stream.
Check Point Harmony Suite, focused on endpoint security, operates within a substantial but competitive market. This segment, while experiencing growth, is characterized by the presence of many established vendors, indicating a mature landscape.
Harmony Suite likely serves as a significant cash cow for Check Point, leveraging its existing customer relationships and the persistent demand for robust endpoint protection solutions. The company's strong market position contributes to consistent revenue generation in this area.
In 2023, Check Point reported its security software and cloud revenue reached $2.36 billion, with endpoint and cloud security being key contributors. This demonstrates the financial strength derived from its comprehensive security offerings, including Harmony.
Data Security Solutions
Check Point's data security solutions represent a cornerstone of their enterprise offerings. This segment, while perhaps not experiencing explosive growth, benefits from the unwavering need for robust data protection and regulatory compliance.
The consistent demand for these services translates into a stable revenue stream and a strong market share among Check Point's existing client base. In 2023, Check Point reported that its security solutions, including data security, contributed significantly to its overall revenue. For instance, their cloud security segment, which often encompasses data protection, saw substantial growth, indicating the market's ongoing commitment to securing digital assets.
- Stable Revenue: Data security solutions provide a predictable and consistent revenue stream due to ongoing client needs.
- High Market Share: Check Point maintains a strong position within the data security market, leveraging its established client relationships.
- Fundamental Need: The essential nature of data protection ensures sustained demand, even in mature markets.
- Compliance Driver: Increasing regulatory requirements worldwide further bolster the demand for comprehensive data security.
Security Management Solutions (On-Premise)
Check Point's on-premise security management solutions represent a mature business segment, often categorized as Cash Cows within the BCG Matrix. These offerings continue to generate significant and stable revenue for the company, largely due to their established presence in many large enterprises that have substantial investments in existing on-premise infrastructure.
Despite the growing trend towards cloud security, organizations with stringent compliance mandates or those in regulated industries often maintain their preference for on-premise solutions. This enduring demand ensures a consistent cash flow for Check Point. For instance, in 2023, Check Point reported total revenue of $2.4 billion, with a significant portion still attributable to its established security management products.
- Stable Revenue Generation: The entrenched nature of on-premise deployments provides a predictable and reliable income stream.
- Mature Market Position: These solutions benefit from high brand recognition and long-standing customer relationships.
- Cash Flow Contribution: Profits generated from these mature products can be reinvested into high-growth areas like cloud security.
- Customer Retention: Organizations reliant on on-premise infrastructure are less likely to switch providers quickly, ensuring continued sales.
Check Point's legacy firewall products are a prime example of a Cash Cow, consistently generating substantial revenue due to their established market share and high profit margins. These foundational offerings continue to be a significant contributor to the company's financial stability, as evidenced by their strong performance in the network security segment.
Security subscriptions form another robust Cash Cow for Check Point, delivering predictable and growing recurring revenue. The company's substantial investment in and expansion of these services, reflected in their increasing subscription revenue, highlights their reliability and importance to Check Point's business model.
Check Point's on-premise security management solutions, while in a mature market, continue to function as significant Cash Cows. Their deep integration within enterprise environments and the ongoing need for compliance ensure a stable and predictable revenue stream, allowing for reinvestment into newer growth areas.
| Product Category | BCG Matrix Status | Key Characteristics | 2023 Revenue Contribution (Illustrative) |
|---|---|---|---|
| Legacy Firewalls | Cash Cow | High market share, mature market, strong profit margins | Significant portion of Network Security revenue |
| Security Subscriptions | Cash Cow | Predictable recurring revenue, established market position | $1.48 billion (Subscription and other recurring) |
| On-Premise Management | Cash Cow | Stable revenue, high customer retention, mature market | Contributed to overall $2.4 billion total revenue |
Delivered as Shown
Check Point Software BCG Matrix
The Check Point Software BCG Matrix you are previewing is the precise, fully formatted report you will receive immediately after purchase. This comprehensive analysis, designed for strategic decision-making, contains no watermarks or sample data, offering you direct access to expert-level insights. Once acquired, this document is ready for immediate integration into your business planning, presentations, or competitive strategy discussions.
Dogs
Certain older or less advanced hardware appliances from Check Point, particularly those not slated for the Quantum Force refresh, likely fall into the 'Dog' quadrant of the BCG Matrix. These products face diminishing relevance as the market increasingly favors newer, more integrated, or cloud-native security solutions.
The market for these legacy appliances is characterized by low growth prospects and a shrinking market share. For instance, as of late 2024, Check Point's focus has heavily shifted towards its Quantum Security Gateways and cloud-delivered security services, indicating a strategic move away from older hardware lines.
Niche or discontinued standalone products within Check Point's portfolio, those not fitting the unified Infinity Platform, are likely candidates for the Dogs quadrant. These might be older solutions with limited market adoption and facing declining demand, offering negligible growth prospects. For instance, a legacy VPN appliance with a small customer base and no clear upgrade path would fit here.
Certain legacy or highly customized professional services from Check Point Software, particularly those requiring extensive manual intervention or tailored solutions for specific clients, may fall into the Dogs category. These services, while crucial for maintaining existing customer relationships, often struggle with scalability and can incur high overhead costs, limiting their profit potential and future growth prospects.
Less Adopted Legacy Software Modules
Less adopted legacy software modules within Check Point’s portfolio, particularly those not slated for integration into the AI-driven Infinity Platform, likely occupy the Dogs quadrant of the BCG Matrix. These could include older endpoint security solutions or specific network management tools that are being phased out. For instance, if a legacy management console, designed for a previous generation of hardware, sees declining adoption as customers migrate to newer, cloud-integrated solutions, it would fit this category.
These modules often represent a drain on development and support resources without substantial market growth or a clear path to future relevance. While specific figures for individual legacy modules are not publicly disclosed, Check Point’s overall shift towards its unified Infinity Platform, which integrates threat intelligence, prevention, and response across all security domains, indicates a strategic move away from siloed, older technologies. The company's focus on AI and automation in its newer offerings underscores the diminished prospects for these less integrated legacy components.
- Declining Market Share: Legacy modules that are not being actively updated or integrated into newer platforms experience a natural decline in adoption as newer, more capable solutions emerge.
- Low Growth Prospects: Without significant investment or a clear roadmap for innovation, these modules are unlikely to see substantial market growth.
- Resource Drain: Maintaining and supporting older software can divert valuable engineering and operational resources that could be better allocated to more strategic, high-growth areas like the Infinity Platform.
- Strategic Obsolescence: As the cybersecurity landscape evolves rapidly with AI and cloud adoption, legacy systems that cannot keep pace risk becoming strategically obsolete.
Products with Limited Global Reach or Regional Specificity
Products with limited global reach or regional specificity are often categorized as Dogs in the BCG Matrix. These are offerings that haven't gained significant traction worldwide or are designed to meet very particular local regulations, making them less appealing for broader markets. For instance, a cybersecurity solution designed exclusively for a niche compliance framework in one country might fall into this category. These products typically have low market share and face limited growth opportunities, making them candidates for divestment or careful management to minimize losses.
In 2024, companies often re-evaluate their product portfolios. Products with limited global reach, especially those requiring constant updates for region-specific mandates, can become a drain on resources. Consider a scenario where a company invested heavily in a specialized data privacy tool for a single European Union member state. If that market doesn't expand or the regulations change unfavorably, the product's revenue might stagnate or decline, placing it firmly in the Dog quadrant.
Key characteristics of these products include:
- Low Market Share: They fail to capture a substantial portion of their potential market, even within their specialized niche.
- Limited Growth Potential: The underlying market is either small or not expected to expand significantly.
- High Maintenance Costs: Catering to specific regional needs can necessitate ongoing, costly adjustments.
- Lack of Scalability: The business model is often not easily transferable to other regions or markets.
Older hardware appliances from Check Point, particularly those not part of the Quantum Force refresh, likely reside in the Dog quadrant. These products face declining relevance as the market shifts towards newer, integrated, or cloud-native security solutions, with low growth prospects and shrinking market share. Check Point's 2024 strategic emphasis on Quantum Security Gateways and cloud services further highlights this move away from older hardware lines.
Legacy software modules not integrated into the AI-driven Infinity Platform, such as older endpoint security or network management tools, also fall into the Dog category. These often represent a drain on development and support resources without significant market growth or future relevance. The company's focus on AI and automation in newer offerings underscores the diminishing prospects for these less integrated legacy components.
Products with limited global reach or regional specificity, failing to gain significant worldwide traction or designed for niche local regulations, are also classified as Dogs. These offerings typically have low market share and limited growth opportunities, making them candidates for divestment or careful resource management. For instance, a specialized data privacy tool for a single EU member state that doesn't expand or faces unfavorable regulatory changes would fit this description.
These "Dog" products are characterized by low market share, limited growth potential, high maintenance costs, and a lack of scalability. They often require significant resource allocation for support and updates without generating substantial returns, making them strategic liabilities rather than assets in a rapidly evolving cybersecurity market.
Question Marks
Check Point Software is identifying Enterprise Risk Management (ERM) solutions as a key growth driver, signaling a market with substantial upward potential. This suggests a high-growth environment where new entrants or those with developing offerings can capture significant share.
Given ERM's relatively nascent stage as a distinct technology portfolio, Check Point's current market penetration might be modest. This positions ERM within the BCG Matrix as a Question Mark, requiring strategic investment to capitalize on its high-growth market prospects and potentially move it towards a Star.
Check Point's Secure Access Service Edge (SASE) solutions are positioned within its emerging technologies, reflecting a dynamic and expanding market segment. This strategic placement within the Infinity Platform's hybrid mesh architecture indicates a focus on future growth and integration capabilities.
The SASE market itself is experiencing significant expansion, with adoption rates accelerating as businesses increasingly rely on integrated cloud-delivered security and networking. This high growth potential suggests Check Point's SASE offerings could represent a future Stars category, provided they can capture substantial market share against established players.
The burgeoning field of AI Makers Protection, or Generative AI Security, represents a critical new frontier in cybersecurity. As generative AI tools become more sophisticated and accessible, they are increasingly weaponized by cybercriminals for advanced phishing campaigns, malware creation, and more insidious attacks. This rapid evolution positions AI Makers Protection as a high-growth, albeit nascent, market segment.
Check Point Software is actively investing in AI-powered security innovations to address these emerging threats. However, in this relatively new market, their current market share in AI Makers Protection and GenAI Security might still be establishing itself. This dynamic places it squarely in the 'Question Mark' category of the BCG matrix, indicating potential for significant growth but also requiring strategic investment and development to capture market leadership.
Advanced Threat Prevention for Emerging Threats (e.g., Quantum Threats)
Check Point's strategy centers on a prevention-first approach, proactively tackling emerging threats like those powered by AI and the future possibility of quantum computing. This positions them well for a high-growth market, though their current share in these very nascent segments might be small.
The market for advanced threat prevention, particularly against future threats like quantum computing, is projected for significant expansion. For instance, the quantum computing market itself is expected to reach tens of billions of dollars by the early 2030s, indicating the potential scale of security solutions needed. Check Point's investment in research and development for these areas is crucial for capturing future market share.
To elevate its position in these cutting-edge threat prevention niches from a Question Mark to a Star, Check Point needs to demonstrate substantial market penetration and technological leadership. This involves not only developing robust solutions but also securing early adoption and establishing a strong competitive advantage as these markets mature.
- Focus on Prevention: Check Point's core philosophy addresses evolving threats, including AI-driven and potential quantum computing attacks.
- High-Growth Market: The segment for advanced, future-oriented threat solutions is experiencing rapid growth.
- Current Market Share: Check Point's share in these very new and developing niches may currently be limited.
- Investment Requirement: Significant investment is needed for Check Point to establish a leading position (Star) in these emerging threat landscapes.
Acquired Technologies (e.g., Veriti)
Check Point Software recently acquired Veriti, a move designed to bolster its Infinity platform. This acquisition aligns with Check Point's strategy to enhance its cybersecurity architecture through advanced technologies.
Technologies like Veriti, while possessing significant growth potential within Check Point's unified ecosystem, are initially positioned as Question Marks in the BCG Matrix. This classification stems from their nascent market share under Check Point's purview, necessitating strategic integration and investment to cultivate their future success.
- Veriti Acquisition: Check Point's acquisition of Veriti aims to enhance its Infinity platform's capabilities.
- High Growth Potential: Newly acquired technologies like Veriti are seen as having high growth potential within Check Point's integrated cybersecurity offerings.
- Initial Market Share: These technologies are initially considered Question Marks due to their developing market share within Check Point's broader platform.
- Strategic Integration: Successful growth for Veriti and similar acquisitions relies on strategic integration and continued investment from Check Point.
Question Marks in Check Point's portfolio represent areas with high market growth potential but currently low market share. These are often new technologies or emerging markets where significant investment is required to gain traction and leadership. Without proper strategic focus and capital allocation, these ventures risk remaining underdeveloped or becoming failures.
Check Point's investment in AI Makers Protection and Generative AI Security exemplifies a Question Mark strategy. The market for AI security is rapidly expanding, driven by the increasing sophistication of cyber threats. However, Check Point's current market share in this nascent field necessitates substantial R&D and market development to transform these offerings into dominant Stars.
Similarly, the acquisition of Veriti positions its advanced technology as a Question Mark. While Veriti's capabilities are expected to enhance Check Point's Infinity platform and tap into a growing market, its initial market share under Check Point requires strategic integration and ongoing investment to realize its full potential and move towards a Star status.
The company's focus on advanced threat prevention, including solutions for future threats like quantum computing, also falls under the Question Mark category. The market for these forward-looking security solutions is projected for substantial growth, but Check Point's current penetration in these highly specialized niches is still developing, demanding strategic investment to secure future market leadership.
| Category | Market Growth | Market Share | Strategic Implication |
|---|---|---|---|
| AI Makers Protection / GenAI Security | High | Low | Requires significant investment for market capture and leadership. |
| Advanced Threat Prevention (Quantum Computing Focus) | High | Low | Needs R&D and early adoption strategies to build share. |
| Veriti (Post-Acquisition) | High | Low (within Check Point's portfolio) | Strategic integration and investment are key to growth. |
BCG Matrix Data Sources
Our BCG Matrix leverages comprehensive market data, including financial reports, industry growth rates, and competitor analysis, to accurately position each product.