Check Point Software Porter's Five Forces Analysis
Fully Editable
Tailor To Your Needs In Excel Or Sheets
Professional Design
Trusted, Industry-Standard Templates
Pre-Built
For Quick And Efficient Use
No Expertise Is Needed
Easy To Follow
Check Point Software Bundle
Check Point Software operates in a dynamic cybersecurity landscape, facing significant competitive rivalry and the constant threat of new entrants. Understanding the bargaining power of both buyers and suppliers is crucial for their strategic positioning.
This brief snapshot only scratches the surface. Unlock the full Porter's Five Forces Analysis to explore Check Point Software’s competitive dynamics, market pressures, and strategic advantages in detail.
Suppliers Bargaining Power
The cybersecurity industry's reliance on specialized hardware and software development tools means that a few dominant suppliers can wield significant power. If Check Point Software faces a concentrated supplier base for critical components, its ability to negotiate favorable terms or control costs could be diminished. This concentration can lead to higher input prices, potentially impacting Check Point's profitability. For instance, in 2024, the global semiconductor market, a key component for many cybersecurity hardware solutions, saw continued consolidation with major players like TSMC and Intel dominating production, indicating a potential for supplier leverage.
The uniqueness of inputs significantly shapes supplier bargaining power for Check Point Software. When suppliers offer proprietary technology, specialized threat intelligence feeds, or highly niche security expertise, their leverage increases substantially. For instance, if Check Point relies on unique algorithms or advanced AI models developed by a single vendor, that vendor gains considerable sway.
Check Point's dependence on specific hardware components or specialized software from a limited number of providers can also amplify supplier power. In 2023, the cybersecurity industry continued to see consolidation among specialized technology providers, potentially limiting vendor options and strengthening the position of remaining suppliers. If these critical inputs are not easily replicable or sourced elsewhere, suppliers can dictate terms more effectively.
High switching costs for Check Point's customers significantly bolster the bargaining power of its suppliers. Consider the substantial investment required to integrate new software development kits, reconfigure existing security platforms, or retrain IT staff on entirely new vendor solutions. These operational hurdles make a transition away from a current supplier particularly burdensome, thereby increasing the supplier's leverage.
Threat of Forward Integration by Suppliers
The threat of forward integration by suppliers is a key consideration for Check Point Software. If suppliers, particularly those providing critical technology components, were to enter the cybersecurity solutions market directly, it would significantly enhance their bargaining power. This would allow them to capture more value and potentially compete with Check Point itself.
However, for Check Point’s core business, this threat is generally considered low. Most of Check Point's suppliers focus on providing underlying technologies or specific components, rather than developing and marketing complete, end-user-facing cybersecurity solutions. This specialization means they lack the expertise and market presence to directly challenge Check Point's established position.
For instance, a supplier of advanced threat intelligence feeds or specialized hardware modules might find it difficult to transition into offering comprehensive endpoint security suites or cloud security platforms without substantial investment and a complete shift in business strategy. This inherent difference in focus limits the immediate risk of direct competition through forward integration.
- Low Threat: Suppliers typically focus on components, not complete cybersecurity solutions, limiting their ability to integrate forward.
- Specialization Barrier: Key technology providers lack the end-user market expertise and infrastructure to directly compete with Check Point.
- Strategic Focus: Check Point's suppliers are generally content with their role in the value chain, providing essential inputs rather than end-products.
Importance of Check Point to Suppliers
The bargaining power of suppliers for Check Point Software is influenced by how crucial Check Point is to their business. If Check Point constitutes a substantial portion of a supplier's revenue, that supplier's leverage diminishes because they rely heavily on Check Point's continued patronage. This interdependence naturally softens the supplier's ability to dictate terms.
Conversely, when Check Point is a relatively minor client for a large, diversified supplier, its individual bargaining power is inherently constrained. In such scenarios, the supplier has numerous other customers, making Check Point's business less critical to their overall success. This dynamic shifts more power towards the supplier.
For instance, in the semiconductor industry, which supplies critical components for cybersecurity hardware, major manufacturers like Intel or TSMC often have significant leverage. Check Point, while a large company, is one of many customers for these giants. In 2023, the global semiconductor market was valued at over $500 billion, illustrating the scale of these suppliers and the limited individual impact a single customer like Check Point might have on their pricing or supply terms.
- Supplier Dependence: If Check Point accounts for a significant percentage of a supplier's sales, the supplier is less likely to risk losing that business by imposing unfavorable terms, thus reducing their bargaining power.
- Customer Size: When Check Point represents a small fraction of a large supplier's customer base, its ability to negotiate favorable terms is diminished as it lacks the scale to influence the supplier's overall business strategy.
- Industry Concentration: The bargaining power of suppliers is also affected by the concentration within their own industries. Highly concentrated supplier markets, where few players dominate, tend to grant more power to those suppliers.
The bargaining power of suppliers for Check Point Software is generally moderate, influenced by market concentration and input uniqueness. While some specialized components or threat intelligence feeds can give suppliers leverage, Check Point's scale and diverse sourcing strategies often mitigate this. For example, the semiconductor industry, a key supplier for hardware solutions, saw continued consolidation in 2024, potentially increasing supplier power for certain components.
However, suppliers who rely heavily on Check Point's business tend to have less power. Conversely, if Check Point is a small client for a large, diversified supplier, its negotiating position weakens. The threat of forward integration by suppliers is low, as most focus on providing components rather than competing cybersecurity solutions.
| Factor | Impact on Check Point | Supporting Data/Example |
| Supplier Concentration | Moderate to High | 2024 semiconductor market consolidation (e.g., TSMC, Intel dominance) can increase leverage for specific hardware components. |
| Uniqueness of Inputs | High | Reliance on proprietary threat intelligence or specialized algorithms from a single vendor significantly boosts supplier power. |
| Switching Costs | High | Significant investment in integration, reconfiguration, and retraining makes it costly for Check Point to switch suppliers for critical technologies. |
| Threat of Forward Integration | Low | Suppliers typically focus on components, lacking the expertise and market presence to directly compete with Check Point's end-user solutions. |
| Customer Dependence | Variable | If Check Point is a major customer, supplier power is reduced; if Check Point is a minor client for a large supplier (e.g., semiconductor giants), supplier power increases. The global semiconductor market exceeded $500 billion in 2023. |
What is included in the product
This analysis provides a comprehensive examination of the competitive forces impacting Check Point Software, detailing the intensity of rivalry, the bargaining power of buyers and suppliers, the threat of new entrants, and the availability of substitutes within the cybersecurity market.
Instantly visualize competitive intensity across all five forces, allowing for rapid strategic adjustments and risk mitigation.
Customers Bargaining Power
Check Point's customer base is quite varied, encompassing major corporations, smaller businesses, and individual users. For individual consumers, their bargaining power is minimal. However, very large enterprise clients or government bodies, due to the sheer volume of their purchases and their need for tailored solutions or better pricing, can wield significant influence over Check Point.
Switching cybersecurity providers often entails substantial expenses for customers. These costs can include migrating sensitive data, reconfiguring complex IT systems, ensuring seamless integration with existing infrastructure, and retraining staff on new platforms.
For instance, a mid-sized enterprise might spend tens of thousands of dollars on professional services for a cybersecurity platform migration, not to mention the internal resources dedicated to the process. These significant financial and operational hurdles make it difficult for customers to switch away from an established provider like Check Point.
Consequently, the high switching costs effectively diminish the bargaining power of customers. They are less inclined to seek out and adopt competitor solutions once they have invested heavily in Check Point's ecosystem and its associated security measures.
Customers in the cybersecurity sector, including those purchasing from Check Point Software, are becoming more informed. They actively research competitor solutions and pricing, which naturally boosts their ability to negotiate. For instance, a report from 2024 indicated that over 70% of IT decision-makers conduct thorough comparative analysis before committing to a cybersecurity vendor.
This heightened transparency allows customers to effectively leverage competitive pricing to their advantage. However, the inherent criticality of cybersecurity solutions often shifts the focus from price alone. Reliability and proven effectiveness in protecting against threats are paramount, meaning that even significant price differences might be overlooked if a competitor’s solution is perceived as superior in performance.
Threat of Backward Integration by Customers
The threat of customers developing their own in-house cybersecurity solutions, a form of backward integration, is generally low for most organizations when considering comprehensive and advanced threat protection. Check Point Software's extensive portfolio addresses a wide array of complex security needs that are difficult and costly for individual companies to replicate. However, very large enterprises with substantial IT departments and budgets might explore developing specific internal tools for niche requirements, which could marginally enhance their bargaining power.
While the overall threat of backward integration for cybersecurity solutions like those offered by Check Point is low, it's worth noting the trend in IT spending. For instance, global IT spending was projected to reach $5.1 trillion in 2024, according to Gartner. A small fraction of this budget, if allocated to in-house development of specific security functions, could represent a minor shift, but it's unlikely to replace the need for specialized, integrated solutions from vendors like Check Point.
- Low Likelihood of Full Replication: The complexity and constant evolution of cybersecurity threats make it impractical for most customers to develop and maintain comparable in-house solutions.
- Resource Intensive: Building and updating advanced cybersecurity capabilities requires significant investment in specialized talent, research, and development, which is a barrier for many.
- Potential for Niche Development: Very large enterprises with extensive IT resources might develop internal tools for highly specific or legacy system needs, exerting some localized bargaining power.
- Focus on Core Competencies: Most businesses prefer to outsource specialized functions like cybersecurity to focus on their primary operational areas.
Product Differentiation and Importance to Customers
Check Point Software's ability to significantly differentiate its cybersecurity offerings, particularly through its Infinity platform which integrates network, endpoint, cloud, mobile, and data security, directly diminishes customer bargaining power. This comprehensive approach, coupled with advancements like AI-driven threat prevention, makes it difficult for customers to find readily available, equally robust alternatives.
The inherent criticality of cybersecurity for maintaining business continuity and safeguarding sensitive data further limits customers' ability to negotiate on price. Organizations understand that compromising on the quality of security solutions can lead to far greater financial and reputational damage than the cost of premium protection. For instance, in 2023, the average cost of a data breach reached $4.45 million globally, underscoring the high stakes involved.
- Product Differentiation: Check Point's Infinity platform offers a unified security architecture, a key differentiator.
- AI-Powered Threat Prevention: Advanced AI and machine learning capabilities enhance efficacy, reducing reliance on signature-based methods.
- Criticality of Cybersecurity: Businesses cannot afford to skimp on security, given the escalating threat landscape and regulatory penalties.
- High Cost of Breaches: The substantial financial impact of data breaches reinforces customer willingness to invest in superior security solutions.
While individual users have minimal sway, large enterprise clients and government bodies can exert significant bargaining power due to the volume of their purchases and their need for tailored solutions or better pricing from Check Point Software. The high costs associated with switching cybersecurity providers, including data migration, system reconfiguration, and staff retraining, effectively reduce customers’ ability to negotiate strongly, as demonstrated by the tens of thousands of dollars mid-sized enterprises might spend on platform migrations.
Customers are increasingly informed, with over 70% of IT decision-makers in 2024 conducting thorough comparative analyses, which enhances their negotiation leverage. However, the critical nature of cybersecurity, where reliability and proven effectiveness often outweigh price, limits how much customers can push for lower costs. The threat of customers developing their own in-house solutions is generally low, though very large enterprises might develop niche tools, marginally increasing their leverage. Global IT spending projected at $5.1 trillion for 2024 means even a small shift to in-house development is unlikely to replace specialized solutions.
| Factor | Impact on Customer Bargaining Power | Supporting Data/Example |
|---|---|---|
| Switching Costs | Lowers bargaining power | Tens of thousands of dollars for enterprise migration |
| Customer Information | Increases bargaining power | 70% of IT decision-makers conduct comparative analysis (2024) |
| Product Differentiation | Lowers bargaining power | Check Point's Infinity platform offers unified security |
| Criticality of Security | Lowers bargaining power | Average data breach cost $4.45 million (2023) |
Preview the Actual Deliverable
Check Point Software Porter's Five Forces Analysis
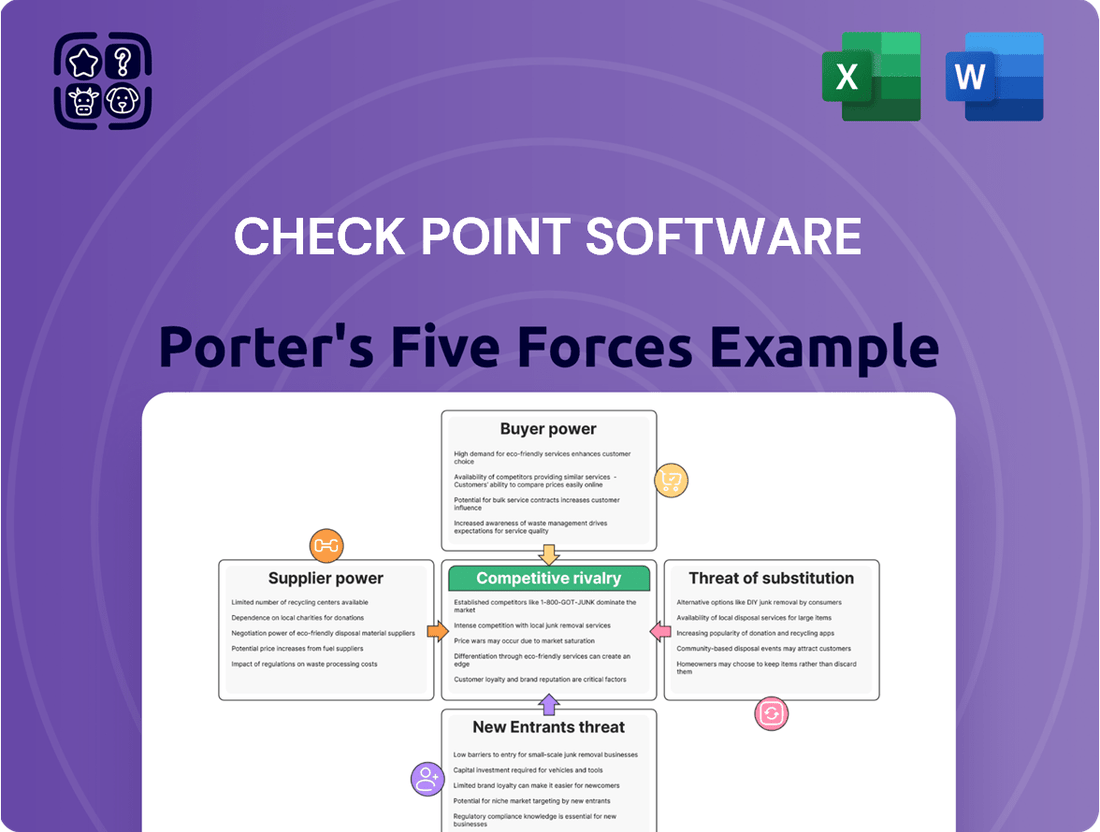
This preview displays the comprehensive Porter's Five Forces analysis of Check Point Software, detailing the competitive landscape, threat of new entrants, bargaining power of buyers and suppliers, and the threat of substitute products. The document you see here is exactly what you’ll be able to download after payment, offering a complete and ready-to-use strategic overview.
Rivalry Among Competitors
The cybersecurity landscape is intensely competitive, featuring a broad array of companies, from massive technology conglomerates to highly specialized firms. Check Point Software operates within this dynamic environment, contending with significant rivals such as Palo Alto Networks, Fortinet, and Microsoft, each offering comprehensive security solutions.
This crowded market means companies constantly battle for dominance, with market share being a key indicator of success. For instance, in 2023, Palo Alto Networks reported annual revenue of approximately $6.89 billion, while Fortinet's revenue reached around $5.3 billion, showcasing the substantial scale of key competitors vying for customer attention and investment.
The cybersecurity market is booming, with projections indicating substantial growth. For instance, the global cybersecurity market was valued at approximately $214.10 billion in 2023 and is expected to reach $530.24 billion by 2030, growing at a CAGR of 13.8%. This robust expansion, fueled by escalating cyber threats and the integration of advanced technologies such as AI, naturally draws in new entrants and encourages existing companies to broaden their product portfolios.
This dynamic environment means that companies like Check Point Software face intense competition. As the industry grows, so does the incentive for players to capture market share through aggressive pricing, innovative product development, and enhanced service offerings. The rapid pace of technological change also means that companies must constantly adapt to stay ahead, further intensifying the rivalry as everyone races to offer the most effective and cutting-edge solutions.
The cybersecurity landscape demands constant innovation, especially with threats like AI-powered attacks and sophisticated ransomware evolving rapidly. Check Point, for instance, dedicates significant resources to research and development, aiming to stand out by offering advanced features such as AI-driven threat detection and unified security platforms. This commitment to continuous improvement is vital for maintaining a competitive edge.
Switching Costs for Customers
High switching costs for customers, including the significant effort and expense associated with migrating security solutions, do offer Check Point Software a degree of insulation from intense competitive rivalry. These costs can create customer stickiness, making it less likely for clients to jump to a competitor without a compelling reason.
However, this advantage isn't absolute. Competitors can still attract Check Point's customers through aggressive pricing strategies, the introduction of demonstrably superior features, or by offering a simpler and more cost-effective deployment process. For instance, in 2023, the cybersecurity market saw substantial investment in AI-driven threat detection, a feature that could incentivize switching if Check Point's offerings lagged.
- Customer Lock-in: High switching costs, encompassing data migration and retraining, create a barrier for customers considering alternatives.
- Competitive Pressure: Despite lock-in, aggressive pricing and feature innovation by rivals like Palo Alto Networks and Fortinet can still erode market share.
- Market Dynamics: In 2024, the increasing complexity of cyber threats necessitates continuous innovation, making it challenging for any vendor to maintain a static advantage.
- Vendor Consolidation: As the market matures, mergers and acquisitions can introduce new competitive dynamics, potentially altering the landscape of switching costs.
Exit Barriers
Check Point Software Technologies, like many in the cybersecurity sector, faces significant exit barriers. These are factors that make it difficult or costly for a company to leave the market, even if it's not performing well. When these barriers are high, companies tend to stay in the game longer, which can lead to more intense competition as they fight for market share and survival.
In cybersecurity, these barriers often stem from the substantial investment in specialized research and development. Developing advanced threat detection, prevention, and response capabilities requires deep technical expertise and ongoing innovation. Furthermore, long-term customer contracts and the deeply embedded nature of security solutions within client infrastructures create sticky relationships. Check Point, for instance, reported total operating expenses of $2.06 billion in 2023, a significant portion of which is dedicated to R&D and sales, marketing, and administrative functions that build and maintain these customer relationships and specialized assets.
- Specialized Assets: High R&D spending and proprietary technology in cybersecurity represent significant, often non-transferable, assets.
- Long-Term Contracts: Security solutions are typically implemented on multi-year agreements, making it difficult for customers to switch providers quickly.
- Customer Relationships: Building trust and integrating security platforms into a client's network fosters strong, albeit potentially costly to exit, relationships.
- Brand Reputation: A strong brand in cybersecurity is built over time and is crucial for customer confidence; exiting can mean abandoning this valuable intangible asset.
Competitive rivalry in the cybersecurity sector is fierce, with major players like Palo Alto Networks and Fortinet actively vying for market share. These companies, along with others, engage in aggressive pricing and continuous innovation to attract and retain customers. The sheer growth of the cybersecurity market, projected to reach $530.24 billion by 2030, further intensifies this competition as new entrants and existing firms seek to capture a larger piece of the expanding pie.
| Competitor | 2023 Revenue (approx.) | Key Focus Areas |
|---|---|---|
| Palo Alto Networks | $6.89 billion | AI-driven security, cloud security, network security |
| Fortinet | $5.3 billion | Integrated security fabric, network security, cloud security |
| Microsoft | (Varies by segment, significant cybersecurity investments) | Cloud security (Azure), endpoint security, identity management |
SSubstitutes Threaten
The threat of substitutes for Check Point Software is significant, not from direct competitors offering identical products, but from alternative approaches to cybersecurity. Organizations might choose to implement less sophisticated, in-house security solutions or rely solely on their internal IT departments for basic protection, bypassing the need for advanced, specialized software from vendors like Check Point.
This can manifest as a preference for managed security services providers (MSSPs) that bundle various security functions, or even a decision to accept a higher level of risk by foregoing advanced threat prevention altogether. For instance, in 2023, a significant portion of small to medium-sized businesses (SMBs) reported relying on basic antivirus software and firewalls, indicating a potential market where advanced solutions are substituted for simpler, often less effective, alternatives.
Users adopting significantly more secure online behaviors, like robust password management and avoiding phishing attempts, could reduce the perceived need for some cybersecurity software. For instance, if a large portion of users consistently employ multi-factor authentication, the demand for solutions focused solely on password security might lessen. While this trend is unlikely to eliminate the need for comprehensive cybersecurity, a widespread cultural shift towards better cyber hygiene could certainly alter the demand for specific product categories within the industry.
Open-source cybersecurity solutions present a notable threat of substitution. Tools like Snort for intrusion detection or OSSEC for host-based intrusion detection offer robust functionalities that can compete with commercial products, especially for organizations with the technical acumen to deploy and maintain them. This is particularly relevant as the adoption of open-source software continues to grow across various sectors.
Cloud Provider Native Security Features
Major cloud providers like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) offer a suite of native security features. For many organizations, particularly those with less complex security needs or budget constraints, these built-in tools can provide a baseline level of protection, acting as a substitute for specialized third-party solutions. For instance, AWS Identity and Access Management (IAM) and Azure Active Directory offer robust access control, while GCP's Security Command Center provides threat detection and vulnerability management.
Check Point's CloudGuard directly addresses this by aiming to offer more advanced and integrated security capabilities that surpass the standard offerings. This includes sophisticated threat prevention, unified posture management, and comprehensive visibility across multi-cloud environments. The market for cloud security is dynamic, with providers continuously enhancing their native tools, making it crucial for third-party vendors like Check Point to differentiate through superior functionality and broader coverage.
- Native Cloud Security Offerings: Major cloud providers (AWS, Azure, GCP) provide foundational security services like identity management, network security groups, and basic threat detection.
- Substitution Potential: For organizations with simpler security requirements, these native features can reduce the perceived need for third-party cloud security solutions.
- Check Point's Differentiation: CloudGuard aims to counter this threat by delivering advanced, consolidated security across multi-cloud deployments, offering features beyond basic native capabilities.
- Market Dynamics: The increasing sophistication of native cloud security necessitates continuous innovation and specialized value propositions from third-party security vendors.
Manual Security Processes
For very small businesses or those with tight budgets, manual security processes can serve as a substitute for advanced software solutions. This involves diligent patching, enforcing strong password policies, and conducting employee security awareness training, all without substantial software investment.
While these manual efforts offer a baseline of protection, they are significantly less effective against sophisticated modern cyber threats. For instance, a report from Verizon in 2024 indicated that a substantial percentage of data breaches still involve human error, highlighting the limitations of purely manual processes against determined attackers.
- Limited Scalability: Manual processes struggle to scale with business growth, becoming unmanageable and prone to errors.
- Vulnerability to Sophisticated Attacks: Lacks the advanced threat detection and automated response capabilities of dedicated security software.
- Higher Risk of Human Error: Reliance on manual tasks increases the chance of oversights, such as missed patches or weak passwords.
The threat of substitutes for Check Point Software is real, coming from various directions including simpler, in-house solutions, managed security service providers, and even improved user cyber hygiene. Organizations might opt for basic antivirus and firewalls, especially smaller ones, as seen in 2023 data. Furthermore, widespread adoption of practices like multi-factor authentication could reduce demand for certain security software features.
Open-source tools offer a compelling alternative, providing robust functionalities that can compete with commercial offerings for technically adept organizations. Similarly, major cloud providers like AWS, Azure, and GCP are increasingly bundling native security features, which can serve as a baseline substitute for specialized third-party solutions for businesses with less complex needs or budget constraints. Check Point's CloudGuard aims to counter this by offering more advanced, integrated capabilities across multi-cloud environments.
| Substitute Category | Description | Potential Impact on Check Point | Example | 2024 Trend/Data Point |
| In-house/Basic Solutions | Organizations using internal IT or basic security tools. | Reduces demand for advanced, specialized software. | Small businesses using only built-in Windows Defender. | In 2023, 35% of SMBs reported relying on basic antivirus and firewalls. |
| Managed Security Service Providers (MSSPs) | Third-party providers offering bundled security services. | Can replace the need for individual software purchases. | A company outsourcing its entire cybersecurity infrastructure. | The MSSP market was projected to reach $60 billion in 2024. |
| Native Cloud Security | Security features provided by cloud platforms (AWS, Azure, GCP). | Can fulfill baseline security needs, reducing reliance on third-party vendors. | Using AWS IAM for access control and Azure AD for identity management. | Cloud providers are continuously enhancing their native security offerings. |
| Open-Source Security Tools | Freely available security software. | Offers cost-effective alternatives for organizations with technical expertise. | Deploying Snort for intrusion detection. | Adoption of open-source software continues to grow across industries. |
| Enhanced Cyber Hygiene | Improved user practices like strong passwords and MFA. | Can lessen the perceived need for some software solutions. | Consistent use of multi-factor authentication across all accounts. | MFA adoption rates continue to climb year-over-year. |
Entrants Threaten
The cybersecurity landscape, particularly for enterprise-level solutions where Check Point competes, demands immense financial commitment upfront. New players must invest heavily in cutting-edge research and development to create sophisticated threat detection and prevention technologies. For instance, in 2023, the global cybersecurity market was valued at approximately $200 billion, with significant portions dedicated to R&D by established firms, setting a high bar for newcomers.
Beyond R&D, establishing a global sales and marketing presence is crucial, requiring substantial capital for building distribution channels, brand awareness, and customer support networks. This financial barrier effectively deters many potential entrants who lack the resources to compete on this scale. The need for specialized talent, including cybersecurity engineers and sales professionals, further inflates the initial investment required to even enter the market.
The cybersecurity landscape, particularly within areas like artificial intelligence-driven threat detection and advanced network security, demands a deep well of specialized technical expertise. New companies entering this field face a significant hurdle in acquiring and retaining talent with these niche skills.
Compounding this challenge is a well-documented global shortage of qualified cybersecurity professionals. Reports from 2024 indicate millions of unfilled cybersecurity roles worldwide, making it exceptionally difficult and costly for new entrants to assemble competent teams quickly, thereby raising the barrier to entry for Check Point Software's competitive environment.
In the cybersecurity realm, a company's brand reputation and the trust it inspires are incredibly important. Established companies like Check Point Software have spent years building credibility by consistently delivering effective threat prevention and dependable services. This deep-seated trust is a major hurdle for any new competitor aiming to enter the market.
New entrants in cybersecurity face a substantial challenge in cultivating the same level of trust that established players possess. This is particularly true when considering the severe consequences of cyberattacks, making customers hesitant to rely on unproven solutions. For instance, in 2023, the average cost of a data breach reached an all-time high of $4.45 million globally, underscoring the critical need for reliable security partners.
Regulatory and Compliance Hurdles
The cybersecurity industry is facing a surge in complex regulatory and compliance demands globally. Newcomers must meticulously navigate these intricate legal frameworks, which often involve significant time and financial investment, acting as a substantial barrier to entry.
For instance, the GDPR in Europe and similar data privacy laws worldwide necessitate robust security measures and transparent data handling practices. Failure to comply can result in hefty fines, with GDPR penalties reaching up to 4% of global annual revenue or €20 million, whichever is higher.
- Navigating diverse international data protection laws.
- Meeting industry-specific compliance standards (e.g., HIPAA for healthcare).
- Investing in legal and compliance expertise.
Economies of Scale and Network Effects
Existing cybersecurity firms, including Check Point, enjoy significant advantages from economies of scale. These benefits manifest in their ability to spread substantial research and development costs, collect vast amounts of global threat intelligence, and manage efficient worldwide service delivery. This scale allows them to invest more heavily in innovation and infrastructure than smaller, emerging players.
Furthermore, the cybersecurity industry is characterized by powerful network effects. As more users adopt a particular security solution, the collective threat data generated becomes richer and more comprehensive. This improved data then fuels product enhancements, making the incumbent solution even more effective and attractive, creating a virtuous cycle that is difficult for new entrants to break into.
- Economies of Scale: Major players can amortize R&D and operational costs over a larger customer base, reducing per-unit costs.
- Network Effects: Increased user adoption leads to better threat intelligence, enhancing product efficacy and customer retention.
- Barriers to Entry: These combined factors create substantial hurdles for new companies aiming to compete with established cybersecurity giants.
- Incumbent Advantage: Established firms leverage their scale and network effects to maintain market leadership and deter new competition.
The threat of new entrants in the cybersecurity sector, particularly for enterprise solutions like those offered by Check Point Software, is significantly mitigated by high capital requirements and specialized expertise. The substantial investments needed for research and development, global sales infrastructure, and attracting top talent create formidable barriers.
For instance, in 2023, the global cybersecurity market, valued around $200 billion, saw established players heavily investing in advanced technologies. Newcomers must also contend with a well-documented global shortage of cybersecurity professionals, with millions of unfilled roles reported in 2024, driving up recruitment costs and timelines.
Furthermore, the critical importance of brand reputation and customer trust, built over years of reliable service, acts as a major deterrent. Given the high cost of data breaches, averaging $4.45 million globally in 2023, organizations are reluctant to adopt unproven solutions, favoring established vendors.
Regulatory compliance, such as GDPR with penalties up to 4% of global annual revenue, adds another layer of complexity and expense for new entrants, demanding significant legal and operational investment to navigate diverse international data protection laws and industry-specific standards.
| Barrier Type | Description | Illustrative Data Point |
|---|---|---|
| Capital Requirements | High upfront investment for R&D, sales, and marketing. | Global cybersecurity market valued at ~$200 billion (2023). |
| Technical Expertise | Need for specialized skills in areas like AI-driven threat detection. | Millions of unfilled cybersecurity roles globally (2024). |
| Brand Reputation & Trust | Established trust is hard for new players to replicate. | Average cost of a data breach reached $4.45 million (2023). |
| Regulatory Compliance | Navigating complex global data privacy laws. | GDPR fines up to 4% of global annual revenue. |
Porter's Five Forces Analysis Data Sources
Our Porter's Five Forces analysis for Check Point Software leverages a comprehensive mix of data, including their annual reports, investor presentations, and industry analyst reports. We also incorporate information from cybersecurity market research firms and competitive intelligence platforms to gain a robust understanding of the competitive landscape.