CrowdStrike Porter's Five Forces Analysis
Fully Editable
Tailor To Your Needs In Excel Or Sheets
Professional Design
Trusted, Industry-Standard Templates
Pre-Built
For Quick And Efficient Use
No Expertise Is Needed
Easy To Follow
CrowdStrike Bundle
CrowdStrike's position in the cybersecurity market is shaped by intense rivalry, the threat of new entrants, and the bargaining power of buyers. Understanding these forces is crucial for navigating this dynamic landscape.
The complete report reveals the real forces shaping CrowdStrike’s industry—from supplier influence to threat of new entrants. Gain actionable insights to drive smarter decision-making.
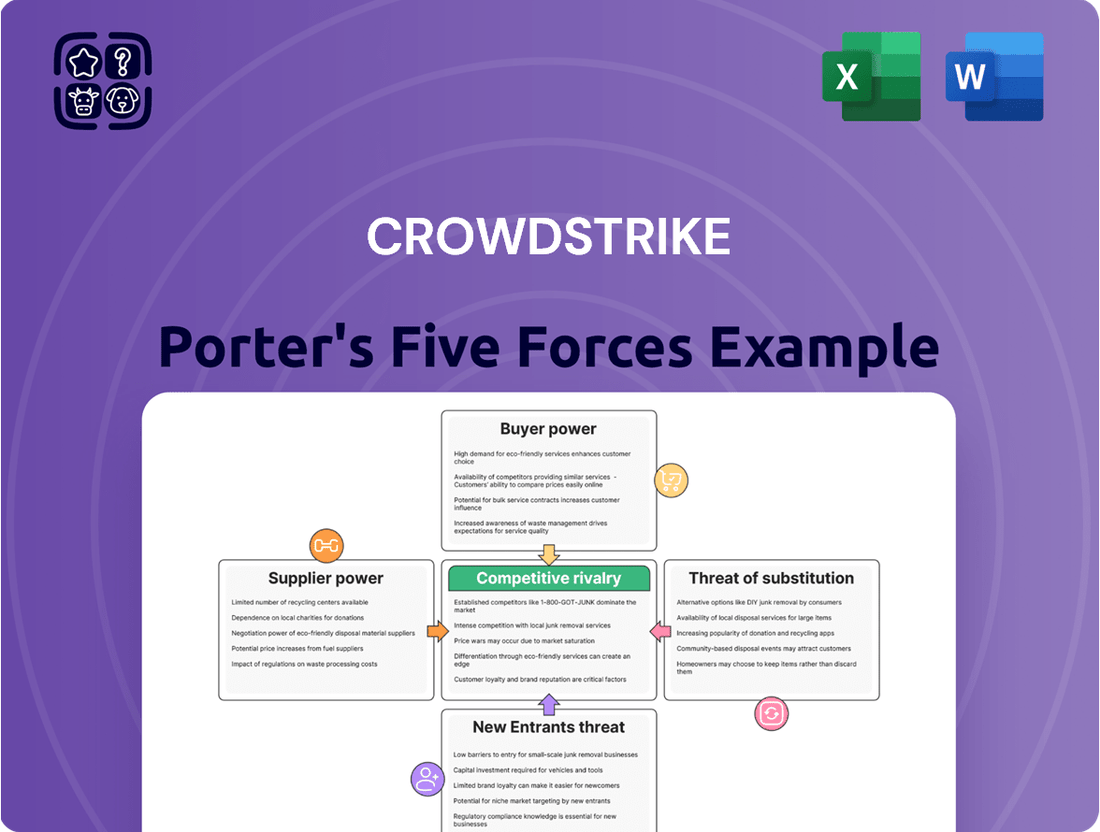
Suppliers Bargaining Power
CrowdStrike's in-house development of its core Falcon platform significantly limits the bargaining power of its suppliers. By controlling its intellectual property and core technology, CrowdStrike reduces its dependence on any single external software or technology component provider. This strategy is crucial for maintaining flexibility and cost control in its operations.
While CrowdStrike develops its core technology internally, it does rely on major cloud infrastructure providers. The concentration of power among a few large cloud service providers, such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP), does introduce some supplier leverage. However, the ability to potentially shift workloads or utilize multi-cloud strategies can mitigate this dependency to a degree.
CrowdStrike's reliance on major cloud infrastructure providers like Amazon Web Services (AWS) and Google Cloud Platform (GCP) significantly influences supplier bargaining power. The sheer scale and competitive nature of these providers, with AWS holding an estimated 31% of the cloud infrastructure market share as of early 2024 and GCP a substantial portion of the remaining, means no single provider can unilaterally dictate terms to a large consumer like CrowdStrike.
This robust competition among cloud giants inherently limits their individual bargaining power over CrowdStrike. The company benefits from the availability of multiple, highly capable alternatives, allowing for potential diversification or even switching of cloud infrastructure partners if pricing or service terms become unfavorable. This dynamic ensures CrowdStrike can negotiate from a position of strength.
The bargaining power of suppliers for CrowdStrike's underlying hardware components, like servers and networking equipment, is generally low. This is because these components are often standardized commodities, meaning there are many manufacturers and sellers available. For instance, in 2024, the global server market saw intense competition, with major players like Dell Technologies, HPE, and Lenovo vying for market share, which inherently limits any single supplier's ability to dictate terms.
Reliance on Highly Skilled Talent
Reliance on highly skilled talent significantly influences the bargaining power of suppliers for cybersecurity firms like CrowdStrike. These specialized employees, particularly those proficient in AI, machine learning, and threat intelligence, are critical to delivering advanced security solutions.
The ongoing global cybersecurity skills shortage, which saw an estimated 4.7 million unfilled positions in 2023 according to Cybersecurity Ventures, directly amplifies the leverage these professionals hold. This scarcity means companies must compete more intensely for top talent, driving up labor costs and potentially impacting profit margins.
- Talent Scarcity: The global cybersecurity workforce gap is a persistent challenge, creating a strong demand for specialized skills.
- Increased Labor Costs: Competition for AI and machine learning experts can lead to higher salaries and benefits packages.
- Impact on Innovation: A tight labor market can slow down product development and the ability to respond to evolving threats.
Open-Source Software and Libraries
CrowdStrike's reliance on open-source software and libraries significantly diminishes supplier bargaining power. These components are typically free and community-driven, meaning no single entity dictates terms or pricing. This widespread availability ensures CrowdStrike can readily access and integrate necessary tools without being beholden to proprietary vendors.
This dynamic is crucial for tech companies like CrowdStrike, which often build complex platforms. For instance, in 2024, the adoption of open-source technologies like Kubernetes for container orchestration and various Python libraries for data analysis remains a cornerstone of efficient software development. The lack of vendor lock-in associated with these open-source assets means CrowdStrike can switch or adapt components with minimal disruption, further weakening any potential supplier leverage.
- Reduced Cost: Open-source software eliminates licensing fees, directly impacting operational expenses.
- Flexibility and Customization: Companies can modify open-source code to fit specific needs, avoiding limitations of proprietary solutions.
- Community Support: Large, active communities often provide robust support and rapid bug fixes, negating the need for costly vendor support contracts.
- Innovation: Open-source fosters rapid innovation through collaborative development, allowing companies to leverage cutting-edge technologies.
CrowdStrike's bargaining power with its suppliers is generally low due to its in-house development of core technologies and the use of standardized, commoditized components. This strategic approach minimizes reliance on any single external provider for critical software or hardware.
While CrowdStrike utilizes major cloud infrastructure providers, the competitive landscape among these giants, such as AWS and Google Cloud, limits their individual leverage. The availability of multiple, capable alternatives allows CrowdStrike to negotiate favorable terms, as demonstrated by AWS's 31% cloud market share in early 2024, indicating a balance of power.
The company's reliance on open-source software further weakens supplier power, as these freely available, community-driven tools eliminate licensing fees and vendor lock-in. This is exemplified by the widespread adoption of technologies like Kubernetes in 2024, enabling flexibility and cost efficiency.
However, CrowdStrike faces significant supplier power in the form of highly skilled cybersecurity talent. The global shortage of these professionals, with an estimated 4.7 million unfilled positions in 2023, amplifies their leverage, driving up labor costs and impacting innovation timelines.
| Supplier Category | CrowdStrike's Leverage | Key Factors | Impact on CrowdStrike |
|---|---|---|---|
| Core Technology Development | High | In-house IP control | Reduced dependence, cost control |
| Cloud Infrastructure (AWS, GCP) | Moderate | Market competition, multi-cloud options | Negotiating power, potential for diversification |
| Hardware Components (Servers) | High | Commoditized market, multiple vendors (e.g., Dell, HPE) | Standardized pricing, limited supplier influence |
| Specialized Talent (AI/ML Experts) | Low | Global skills shortage (4.7M unfilled roles in 2023) | Increased labor costs, competition for talent |
| Open-Source Software | Very High | Free availability, community support, no vendor lock-in | Reduced operational expenses, enhanced flexibility |
What is included in the product
CrowdStrike's Porter's Five Forces analysis dissects the competitive intensity within the cybersecurity market, evaluating threats from new entrants, the bargaining power of buyers and suppliers, the impact of substitutes, and the rivalry among existing players.
Effortlessly visualize competitive pressures with pre-built charts, eliminating the struggle of manual analysis and enabling swift strategic adjustments.
Customers Bargaining Power
Once an organization deeply integrates CrowdStrike's Falcon platform, the effort and expense to switch vendors become significant. This involves migrating vast amounts of security data, re-educating IT and security teams on a new system, and managing the potential for operational disruptions during the transition. These post-implementation hurdles effectively lock customers in, diminishing their ability to bargain for better terms.
The criticality of cybersecurity services significantly impacts the bargaining power of customers. As cyber threats like ransomware and sophisticated malware-free attacks become more prevalent and damaging, businesses view cybersecurity not as an optional expense but as an essential operational requirement. This heightened necessity means customers are less inclined to switch providers based solely on price, as the cost of a breach far outweighs the savings from a cheaper solution. For instance, the average cost of a data breach in 2023 reached $4.45 million globally, a figure that underscores the immense value placed on robust security.
CrowdStrike's impressive customer retention rates, often exceeding 97% gross retention even following significant security events, directly illustrate the bargaining power of its customers. This high loyalty indicates customers find substantial, indispensable value in the Falcon platform, making them highly resistant to switching. Such strong retention significantly diminishes customers' ability to exert downward pressure on pricing or demand unfavorable terms, thereby reducing their bargaining power.
Large Enterprise Customer Base
CrowdStrike's extensive global customer base, which includes numerous large enterprises across diverse sectors, significantly moderates customer bargaining power. While a single large client represents a substantial revenue stream, the sheer breadth of its clientele means no single customer holds a disproportionate amount of sway.
This broad customer adoption, as evidenced by CrowdStrike's strong performance in 2024, means that the loss of any one customer, even a large one, would not critically impact the company's overall financial health or market position. For instance, in fiscal year 2024, CrowdStrike reported a substantial increase in its customer count, further diversifying its revenue base.
- Diversified Customer Portfolio: CrowdStrike serves thousands of customers globally, reducing reliance on any single entity.
- Large Enterprise Penetration: While large enterprises are key, their individual impact is diluted by the overall customer volume.
- Scalability of Services: The platform's ability to scale across many organizations limits the leverage individual customers can exert on pricing or terms.
- Market Leadership: CrowdStrike's dominant position in endpoint security provides a strong negotiating stance against individual customer demands.
Impact of Outages or Performance Issues
While CrowdStrike typically enjoys strong customer loyalty, significant service disruptions, like the one experienced in July 2024, can temporarily shift bargaining power. During such outages, customers may feel compelled to explore alternative cybersecurity providers, even if only to assess their options for greater resilience.
Although CrowdStrike's retention rates generally remain high, these performance-related incidents serve as a reminder that customers can, and do, evaluate their reliance on a single vendor. This can lead to increased scrutiny of service level agreements and a greater willingness to consider diversification strategies to mitigate future risks.
- July 2024 Outage Impact: Incidents like the July 2024 service disruption can temporarily empower customers by highlighting the risks of over-reliance on a single provider.
- Exploration of Alternatives: Even with high retention, such events prompt some customers to actively investigate alternative cybersecurity solutions, increasing their perceived bargaining power.
- Resilience as a Factor: The potential for outages underscores the importance of resilience and diversification for customers, influencing their future vendor selection criteria.
The bargaining power of CrowdStrike's customers is generally low due to high switching costs and the critical nature of cybersecurity. Customers are locked in by the complexity of migrating security data and retraining staff, making them hesitant to switch. The immense cost of data breaches, which averaged $4.45 million globally in 2023, further reduces their incentive to compromise on security solutions for price savings.
CrowdStrike's impressive customer retention, often above 97%, demonstrates that clients find significant, indispensable value in the Falcon platform, limiting their ability to negotiate better terms. This strong loyalty, coupled with a broad, diversified customer base that includes many large enterprises, means no single customer holds disproportionate leverage over CrowdStrike.
However, significant service disruptions, such as the July 2024 outage, can temporarily increase customer bargaining power. These events prompt customers to explore alternatives, highlighting the risks of vendor lock-in and emphasizing the need for resilience, which can influence future vendor selection and negotiation strategies.
| Factor | Impact on Customer Bargaining Power | Supporting Data/Reasoning |
|---|---|---|
| Switching Costs | Low | High costs associated with data migration and retraining. |
| Criticality of Service | Low | Cybersecurity is essential; cost of breach ($4.45M in 2023) outweighs savings from switching. |
| Customer Retention | Low | Rates exceeding 97% indicate high customer satisfaction and perceived value. |
| Customer Base Diversification | Low | Large, diverse customer portfolio dilutes individual customer influence. |
| Service Disruptions (e.g., July 2024) | Temporarily High | Events can lead to exploration of alternatives and increased focus on resilience. |
Preview the Actual Deliverable
CrowdStrike Porter's Five Forces Analysis
This preview showcases the complete CrowdStrike Porter's Five Forces Analysis, identical to the document you'll receive instantly upon purchase. You're viewing the final, professionally formatted report, ensuring no discrepancies or missing information. This means you get the exact, ready-to-use analysis without any placeholders or sample content.
Rivalry Among Competitors
The cybersecurity landscape is fiercely competitive, with CrowdStrike contending against a multitude of formidable players. Established giants like Microsoft Defender for Endpoint, SentinelOne, and Palo Alto Networks are constantly innovating and aggressively pursuing market share, creating a highly dynamic environment.
This intense rivalry means that companies like CrowdStrike must continuously invest in research and development to stay ahead. For instance, in fiscal year 2024, CrowdStrike reported a significant increase in its R&D spending, reflecting the need to counter competitor advancements and maintain its technological edge.
The cybersecurity arena is a hotbed of innovation, with artificial intelligence and machine learning rapidly evolving for both defense and offense. This constant technological churn means companies like CrowdStrike must pour significant resources into research and development just to keep pace, fueling intense rivalry.
For instance, CrowdStrike reported a 30% year-over-year increase in its total revenue for fiscal year 2024, reaching $3.06 billion, highlighting the demand for advanced solutions in this dynamic market. Competitors are also investing heavily, with many focusing on AI-driven threat detection and response to capture market share.
CrowdStrike maintains a strong position in endpoint security, but market share is not static. Competitors like Microsoft, SentinelOne, and Palo Alto Networks are actively gaining traction, indicating a highly dynamic competitive landscape.
This ongoing shift in market share underscores the intense rivalry and the necessity for continuous innovation. CrowdStrike's ability to differentiate its Falcon platform through its cloud-native architecture and AI-driven threat detection is crucial for sustaining its competitive edge.
For instance, in 2023, CrowdStrike reported a substantial increase in its customer base, reaching over 23,000 customers. However, the broader cybersecurity market is experiencing rapid growth, with numerous players vying for dominance, making market share a key battleground.
Consolidation Trend in Cybersecurity
The cybersecurity market is witnessing a significant consolidation trend as customers increasingly favor unified platforms to streamline operations and cut expenses. This shift means competitors are compelled to broaden their offerings, leading to a more intense rivalry for customers committed to integrated security solutions.
This drive for consolidation is evident in recent acquisition activity. For instance, in 2024, various cybersecurity firms announced strategic acquisitions aimed at expanding their platform capabilities. These moves are directly influenced by customer demand for end-to-end security, pushing companies to either acquire complementary technologies or develop them internally to remain competitive.
- Customer Demand for Unified Platforms: Organizations are seeking to reduce the number of security vendors they manage, leading to a preference for integrated solutions that offer broader protection and simplified management.
- Intensified Competition: Cybersecurity vendors are responding by expanding their product portfolios, often through acquisitions, to offer more comprehensive platform solutions, thereby escalating the competition for platform adoption.
- Market Consolidation Drivers: The pursuit of economies of scale, enhanced cross-selling opportunities, and the ability to provide a more compelling value proposition to customers are key factors driving this consolidation trend.
Aggressive Pricing and Incentives
The cybersecurity landscape is intensely competitive, with rivals like Microsoft, Palo Alto Networks, and SentinelOne frequently employing aggressive pricing and incentives to capture market share, particularly among large enterprise clients. These strategies can include offering substantial discounts, flexible payment terms, or bundled services, directly challenging CrowdStrike's pricing power and potentially impacting its profit margins. This pressure is evident as these competitors vie for the same high-value customer base that CrowdStrike targets.
For instance, in 2024, many cybersecurity providers continued to emphasize value-based pricing and extended contract terms to secure long-term customer commitments. This competitive dynamic necessitates that CrowdStrike constantly evaluates its own pricing models and incentive structures to remain attractive to its target market without compromising its financial health.
- Aggressive tactics: Major competitors often use price reductions and special offers to win over large customers.
- Customer retention: Deferred payment options and bundled services are common incentives used to lock in clients.
- Profitability impact: Such competitive pressures can force CrowdStrike to adjust its pricing, potentially affecting its profitability.
- Market share battle: The fight for enterprise clients is fierce, making pricing a critical battleground in the cybersecurity sector.
The competitive rivalry in the cybersecurity sector is exceptionally high, with CrowdStrike facing intense pressure from established players and emerging threats. Competitors like Microsoft Defender for Endpoint, SentinelOne, and Palo Alto Networks are continuously innovating, leveraging AI and expanding their platform capabilities to capture market share.
This dynamic environment forces CrowdStrike to invest heavily in research and development. In fiscal year 2024, CrowdStrike's R&D expenditure increased significantly, underscoring the need to maintain a technological edge against rivals who are also prioritizing AI-driven solutions.
Customer demand for unified security platforms further intensifies this rivalry, pushing vendors to broaden their offerings through acquisitions and internal development. This consolidation trend means companies must offer comprehensive solutions to remain competitive, making pricing and value proposition critical differentiators.
| Competitor | Key Focus Areas | 2024 Market Impact |
|---|---|---|
| Microsoft Defender for Endpoint | Integrated OS security, cloud solutions | Strong enterprise adoption due to bundled offerings |
| SentinelOne | AI-driven endpoint security, autonomous response | Gaining traction with advanced threat detection capabilities |
| Palo Alto Networks | Platform consolidation, network security integration | Expanding platform through acquisitions to meet unified security demand |
SSubstitutes Threaten
Traditional antivirus solutions remain a viable substitute, especially for budget-conscious individuals and smaller businesses. These legacy tools offer foundational malware protection, a critical consideration for a significant segment of the market. For instance, in 2024, while advanced cybersecurity solutions are gaining traction, a substantial portion of small and medium-sized businesses (SMBs) still rely on basic antivirus software due to cost-effectiveness.
However, these traditional offerings present a clear threat due to their inherent limitations. They often lack the sophisticated behavioral analysis, real-time threat intelligence, and rapid response capabilities that are paramount in today's evolving threat landscape. This makes them less effective against zero-day exploits and advanced persistent threats, areas where platforms like CrowdStrike excel.
Large enterprises may consider building extensive in-house security teams and relying on manual processes, bypassing specialized Extended Detection and Response (XDR) platforms like CrowdStrike. This approach often involves using more generic security tools that may not offer the same level of specialized threat detection and response capabilities.
However, the sheer volume and sophistication of cyber threats in 2024 often render purely manual processes and less specialized tools insufficient. The cost and resource drain of maintaining a comprehensive in-house operation to combat advanced persistent threats (APTs) can be substantial, potentially exceeding the investment in a dedicated AI-driven solution.
Network-based security solutions, such as firewalls and intrusion detection systems, act as a potential threat of substitutes for endpoint security by focusing on perimeter defense. While they don't directly replace endpoint protection, a significant investment in these network-centric defenses might lead some organizations to perceive a reduced immediate need for advanced endpoint solutions, especially if they believe their perimeter is sufficiently fortified. This can impact demand for dedicated endpoint security products.
Managed Security Service Providers (MSSPs)
Managed Security Service Providers (MSSPs) present a significant threat of substitutes for CrowdStrike's endpoint detection and response (EDR) solutions. Organizations can opt to outsource their entire cybersecurity infrastructure to MSSPs, which bundle various security services, including endpoint protection, threat detection, and incident response. This comprehensive offering can be more appealing to businesses seeking a turnkey solution rather than managing individual security platforms.
The MSSP market is robust and growing, indicating a strong preference for outsourced security among many businesses. For instance, the global managed security services market was valued at approximately $29.5 billion in 2023 and is projected to reach $74.9 billion by 2030, growing at a compound annual growth rate of 14.3% during this period. This expansion highlights the increasing adoption of MSSPs as a viable alternative to in-house security management.
- Bundled Services: MSSPs offer a complete security package, reducing the need for organizations to procure and integrate separate EDR solutions.
- Cost-Effectiveness: For some businesses, especially small to medium-sized enterprises, outsourcing to an MSSP can be more cost-effective than building and maintaining an in-house security team and infrastructure.
- Expertise Access: MSSPs provide access to specialized cybersecurity expertise that many organizations may lack internally, making them an attractive substitute for direct platform ownership.
Operating System Built-in Security Features
Operating systems like Windows offer built-in security features, such as Microsoft Defender. While these provide a foundational level of defense, they often fall short compared to specialized solutions. For instance, in 2024, while Defender is a significant improvement, advanced persistent threats (APTs) and zero-day exploits continue to bypass such integrated defenses.
These built-in tools typically lack the sophisticated Endpoint Detection and Response (EDR) capabilities, deep threat hunting functionalities, and advanced AI-driven threat analysis that dedicated cybersecurity platforms deliver. This gap means that organizations relying solely on OS-level security are more vulnerable to complex and rapidly evolving cyberattacks.
- Baseline Protection: OS-level security offers fundamental protection against common malware.
- Advanced Threat Gap: Lacks advanced EDR, threat hunting, and AI for sophisticated threats.
- Vulnerability: Reliance on built-in features leaves organizations exposed to modern cyberattacks.
- Specialized Solutions: Dedicated platforms provide superior defense against evolving threats.
While traditional antivirus remains a substitute, its limitations against advanced threats are significant, especially for businesses needing robust protection. Built-in operating system security, like Microsoft Defender, offers baseline defense but often lacks the sophisticated EDR and AI capabilities of specialized platforms, leaving users vulnerable to zero-day exploits. Furthermore, MSSPs present a growing alternative by bundling comprehensive security services, appealing to organizations seeking outsourced expertise and cost-effectiveness, as evidenced by the managed security services market projected to reach $74.9 billion by 2030.
| Substitute Category | Key Characteristics | CrowdStrike's Advantage | Market Trend (2024 Focus) |
|---|---|---|---|
| Traditional Antivirus | Basic malware protection, lower cost | Advanced behavioral analysis, real-time intelligence | Still prevalent in SMBs due to cost, but insufficient for advanced threats |
| OS-Level Security (e.g., Microsoft Defender) | Integrated, foundational defense | EDR, threat hunting, AI-driven analysis | Improving but still susceptible to sophisticated attacks |
| Managed Security Service Providers (MSSPs) | Bundled services, outsourced expertise | Specialized platform capabilities, granular control | Rapid growth, projected $74.9B by 2030, offering a complete security package |
Entrants Threaten
The development of sophisticated cloud-native endpoint and workload protection platforms, heavily reliant on AI and machine learning, demands substantial capital for research and development, alongside specialized technical talent. This significant investment hurdle makes it exceedingly difficult for new companies to enter the market and compete effectively.
In cybersecurity, brand reputation and trust are incredibly important. For instance, CrowdStrike's strong track record, built over years, makes it challenging for newcomers to win over customers, particularly when dealing with sensitive data protection.
New entrants struggle to overcome the established trust that companies like CrowdStrike have cultivated. Gaining market share requires not just a good product, but also demonstrating unwavering reliability, which takes considerable time and consistent performance.
CrowdStrike's immense global customer base, numbering over 23,000 as of early 2024, fuels powerful network effects. The Threat Graph®, which processes trillions of daily endpoint events, provides a data advantage that new entrants cannot replicate.
This vast data pool directly translates to superior threat detection accuracy and faster response times, creating a significant barrier to entry. Competitors would struggle to gather and analyze a comparable volume of real-world threat intelligence.
Regulatory Compliance and Certifications
The cybersecurity industry is a minefield of evolving regulatory requirements and compliance standards, making it a significant barrier for new entrants. Navigating and achieving numerous certifications, such as ISO 27001, SOC 2, or FedRAMP, demands substantial investment and time. For instance, obtaining FedRAMP authorization for cloud-based services can take upwards of 12-18 months and cost hundreds of thousands of dollars, a steep hurdle for emerging players.
These complex regulations and the need for rigorous adherence add considerable cost and time to market entry, effectively raising the barrier. CrowdStrike, for example, maintains a robust portfolio of certifications and attestations, demonstrating its commitment to meeting stringent global security and compliance mandates. This established compliance posture is a significant advantage over any newcomer who would need to replicate this extensive effort.
- Evolving Regulatory Landscape: Cybersecurity is constantly shaped by new laws and standards globally.
- Certification Burden: Obtaining industry-recognized certifications is costly and time-consuming for new companies.
- Compliance Costs: Adhering to complex regulations like GDPR or CCPA requires significant resources.
- Established Players' Advantage: Companies like CrowdStrike have already invested heavily in achieving and maintaining compliance.
Access to Distribution Channels and Partnerships
New entrants face a significant hurdle in replicating CrowdStrike's established distribution channels and strategic partnerships. CrowdStrike has cultivated deep relationships with major cloud providers like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform, along with a vast network of resellers and managed security service providers (MSSPs).
This extensive ecosystem is not easily replicated; it requires substantial time, investment, and proven reliability to secure similar alliances. For instance, as of early 2024, CrowdStrike's Falcon platform is integrated with over 150 technology partners, showcasing the breadth of its reach.
Newcomers attempting to enter the market must overcome the challenge of gaining access to these critical distribution pathways. Without established partnerships, potential customers may be hesitant to adopt solutions from unproven vendors, especially in the cybersecurity space where trust and integration are paramount.
- Established Partnerships: CrowdStrike leverages its strong relationships with cloud giants like AWS, Azure, and GCP for seamless platform integration and broader market reach.
- Reseller and MSSP Network: A robust network of resellers and managed security service providers extends CrowdStrike's sales and support capabilities globally.
- Integration Ecosystem: With over 150 technology partners in early 2024, CrowdStrike offers a comprehensive security ecosystem that is difficult for new entrants to match.
- Barrier to Entry: The significant investment and time required to build a comparable distribution and partnership network create a substantial barrier for new competitors.
The threat of new entrants in the cybersecurity market, particularly for advanced endpoint protection like CrowdStrike's, is significantly mitigated by high capital requirements for R&D and specialized talent. Furthermore, building brand reputation and trust, crucial in this sector, takes years of consistent performance, a hurdle newcomers find difficult to overcome.
CrowdStrike's extensive data advantage, fueled by its Threat Graph processing trillions of daily events and its over 23,000 customers as of early 2024, creates a formidable barrier. New entrants struggle to amass and analyze a comparable volume of real-world threat intelligence, which is essential for superior detection and response capabilities.
Navigating the complex and evolving regulatory landscape, including obtaining certifications like FedRAMP which can cost hundreds of thousands of dollars and take 12-18 months, presents a substantial challenge for new players. CrowdStrike's existing robust compliance posture, encompassing numerous global certifications, further solidifies its advantage.
The difficulty in replicating CrowdStrike's established distribution channels and strategic partnerships with major cloud providers and a vast network of resellers and MSSPs acts as a significant deterrent. With over 150 technology partners integrated into its Falcon platform by early 2024, CrowdStrike offers an ecosystem that is exceptionally hard for new entrants to match.
Porter's Five Forces Analysis Data Sources
Our CrowdStrike Porter's Five Forces analysis is built upon a foundation of comprehensive data, drawing from cybersecurity industry reports, financial filings of key players, and market intelligence platforms. This ensures a robust understanding of competitive dynamics, threat of new entrants, and buyer bargaining power.